In the October 2018 issue of Security Technology Executive magazine, Pierre Bourgeix, who is President of ESI Convergent, wrote that “the next-level technology evolution is coming. Long-awaited and discussed, the full convergence of all systems has now been made feasible by Artificial Intelligence (AI), secured communication, and advancements in physical security technology, or more simply, IP-based technology on the network. Initially, this meant that devices could be connected to one another and, to some limited ability, communicate. In the fully converged future, soon to be the present, this communication will enable far greater intelligence capabilities to protect our organizations from risk and liability in ways previously not possible.”
This past week I was fortunate to have the opportunity to meet with Tracy Reinhold, the Vice President and CSO for Everbridge, who is responsible for advancing the company’s enterprise-level security strategy, Reinhold was in Atlanta hosting a small gathering of regional CSOs, which Everbridge does intermittently around the globe.
Reinhold is an evangelist for the employment of advanced technology to aid in the mitigation of organizational risk for global companies, as well as its advantages for the public sector. He is the former CSO of The Federal National Mortgage Association, commonly known as Fannie Mae, a past VP of Global Investigations at Walmart and a 22-year Associate Executive Assistant Director with the FBI.
Duty of Care
This evolutionary journey from law enforcement through the private sector has sharpened Reinhold’s appreciation of what the collaboration of technology and solid risk analytics bring to the table when the C-Suite looks to calculate its risk tables. Reinhold stresses that mitigating risk and employing technology to reach that end are inexorably linked in today’s business environment. A mitigation strategy is used to provide a viable instant response mechanism.
“There is not a single business in the world that isn’t dependent on some sort of technology. Look at the financial sector; you can’t move that much money manually. It takes technology. So why not harness that same technology to ensure the safety and welfare of the people we care about? If your people are your number one asset, is your organization doing everything possible to protect them,” which Reinhold says brings up the ‘duty of care’ issue. “Duty of care is a hot button issue right now.”
The principle of duty of care is that an organization has an obligation to avoid acts or omissions, which could be reasonably foreseen to injure or harm other people. This means that the organization must anticipate risks for its clients and take care to prevent them coming to harm.
He explains that in the past business continuity and contingencies were much simpler and that the premise for duty of care was not as complex. A company like Acme Tire company had a manufacturing plant, a distribution center and several stores.
“All the employees worked at one of those three locations, so keeping them safe stopped at the gate. Now when we look at the rise of lone and remote workers, what is the expectations of corporate America and those employees regarding their safety and welfare? A company has the perceived responsibility to ensure the welfare of the people working for them maintained whether they are in an office or a remote location. That complicates the issue. This is where solutions like visualization and dynamic locations, along with the ability to use predictive and prescriptive analysis to get ahead of threats is so crucial,” says Reinhold.
The Globalization of Risk
Today’s threats must be taken from a global perspective and not viewed through a myopic lens. Reinhold insists that you can’t just look at the U.S. since almost every company that his group deals with has a global footprint. Global threats manifest themselves differently and a lot of that derives from technology.
“When I was dealing with the global war on terrorism back in my last life, what we realize is a threat could germinate anywhere in the world and manifest itself anywhere in the world that same day. The speed of technology has allowed the bad and the good guys to address this issue almost equally. The challenge I find is when nothing happens a sort of complacency sets in and that complacency can be extremely dangerous, whether it is from a business perspective or from a federal, state or municipal law enforcement perspective,” he says.
Reinhold explains that a lot can be said about how we deal with risk and risk mitigation in both public and private sectors from almost opposite ends of the spectrum. In the private sector, it is viewed as a huge issue since (security and risk) are considered cost centers and a lot of those perceptions are results of CSOs and CISOs inability to articulate the value they bring to the core business. He adds that the negative perception is exacerbated because the CSO fails to seek out executive champions. Ultimately, cost-center verses value-center remains a big issue in corporate security.
He cites as an example that when he was head of security at Fannie Mae in Washington D.C. his department used technology to offset costs of security employing sensors in the lighting systems, destination elevators, integrated access control – all of which reduced the dependence on a physical security footprint.
“We probably saved close to $8 million annually on security costs and at the same time provided a much safer environment for the employees, guests and contractors. So, how do you build the business case for that,” ponders Reinhold. “Well, the way you don’t do it is by being mired in security speak. A), the core business doesn’t understand it and, B) it doesn’t interest them. One of our big issues revolved our capital markets room that did billions of dollars of business each day in trades. I sat down with the head of our capital markets room and asked him what was important to him and what needed to be done to keep the business engine of this organization running? Once you understand that, you can then build your security strategy around what’s important to the business. It makes perfect sense.”
Analyzing and Mitigating Threats
Reinhold sees most pressing threats as nation-state threats, non-nation state actors, with hacktivists rounding out the risk triad. State-sponsored threats used to be the 800-pound gorilla, but he doesn’t think that is the case any longer, with criminal organizations that have been nurtured and matured in these nation-states now emerging as a more lethal global threat since they can pay their minions more.
He believes that the bad actors are just as satisfied by being major disruptors as they are actual thieves, saying that it is often the botched and failed response to a threat or organizational crisis that creates havoc rather than the attack itself.
“Organizations often feel they can manage the message rather than be forthright with their shareholders and customers. An example of that, there was a major retailer who sat on a breach for 16 days then was forced to divulge the information that ultimately severely damaged the stock of the company,” relates Reinhold. “At the same time, a major home improvement store had a similar attack. They handled it very differently by getting ahead of the incident. They were proactive in their messaging so there was not even a blip on the radar related to their stock. Reputational and stock value weren’t impacted, shareholders were happy, employees and customers were happy. There was absolutely no loss of trust in the organization.”
Reinhold points out that both organizations suffered almost identical attacks but the way each handled their respective critical incident management process was completely opposite and the resulting consequences were starkly different. He stresses that responses are ultimately incident agnostic; never mind it being cyber, terrorism, an active shooter event or weather.
“It doesn’t matter. If you don’t have a coordinated response and that response isn’t an enterprise-wide response that utilizes quick and accurate notification of all parties concerned, that’s an issue. A solid communications plan and the technology to carry it out are essential,” emphasizes Reinhold. “It has to be a holistic approach to resolving the issues. If you don’t do that you have disjointed messaging going out to your core customers. The speed and clarity to which you respond to an event to employees, customers and shareholders are key. It’s a numbers game. You are eventually going to be breached whether it is a Point-of-Sale machine or an internal network, it doesn’t matter. What you do afterward does matter.”
Public Space and Smart Cities
Mass notification and emergency communications policy and procedure have changed drastically over the last decade. It is not enough to just muster or alert, but there must be actionable two-way communication, with dynamic location services being the most dynamic change in the market space. The ability to locate people and geo-fence fence areas that allow for targeted notification and response is now an essential element of a unified communications plan. When public safety agencies and the private sector look at a city and its risk threats, it is not enough to just mass notify in the event of an incident.
Gone are the days of the organizational phone tree exercise where a few trusted employees hit the employee phone list and called with the emergency notice.
“Somebody had to make that decision to push out an alert, but if you automate those notifications so you set a series of rules it eliminates the human element and potential confusion. Say, you’re a city, in the event of a hurricane, if these events occur you trigger the appropriate response and notifications will be automatically sent out. Nobody must push a button; it expedites critical information and automates a lot of the response. The data comes into the command center for this mid-sized city and the software reviews the rules the city put into the system saying if this happens then this response automatically triggers instead of calling up the assistant city manager at two in the morning. Your response times increase exponentially, while your recovery time decreases at a similar rate,” explains Reinhold.
Visualization is a Key Component
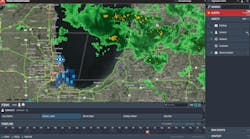
Being able to not only receive the alerts but to see the images from the impacted zone and have that information fed into the command center is also important. This process allows security personnel to overlay elements like traffic patterns, public events calendars and weather forecasts into the analytics model, which in turn enables security and first-responders to follow up that alert and provide the best route of exit. The use of multi-modal means of communication elevates successful response outcomes.
Reinhold was with Fannie Mae in 2017 when Hurricane Harvey, which tied with 2005's Hurricane Katrina as the costliest tropical cyclone on record, inflicted $125 billion in damage, primarily from the devastated Houston metropolitan area and Southeast Texas region. Fannie Mae had single-family and multi-family unpaid loan balances in the impacted areas. He says they were able to put up virtual polygon around Houston and provide to the business the potential impact of the storm on unpaid loan balances.
“This is important because then we are thinking about how we handle loan forbearance for our customers. Taking in all the data gave us a better understanding of the possible size of the impact and the potential recovery strategy for the folks who were impacted. Within 10 minutes we had the (risk) polygon completed and were able to provide our board with a potential risk assessment, which is not the traditional corporate security function. But leveraging your technology can give security executives that leg up,” says Reinhold.
Transitioning to the private sector, Reinhold cites an example of a global consulting firm that might have more than 250,000 employees, 15,000 of which are anchored to a traditional office environment while the bulk of the other consultants are what he calls “dynamic” -- servicing customers around the world. The quandary for executive management is how to keep tabs on their remote consultants and employees and maintain communication in the event of a crisis.
“How do you protect your employees if you don’t know where they are. This is where dynamic location comes into play. You can ping off cell phone information, an IP address, or you can ping into their laptops when they log on. All these options give the organization an opportunity to provide advance warning,” says Reinhold. sharing an example of a company that was able to avoid a crisis in July 2016 when a coup d'état was attempted in Turkey against state institutions, including the government and President Recep Tayyip Erdogan. “This company had several employees preparing to travel overseas through Turkey during the coup. The company was able to alert them at three in the morning before they got on their plane telling them do not take that route but instead get on the Air France flight through Frankfurt. The company was able to avoid catastrophe simply because they were able to dynamically locate these employees when they were not in their offices.”
He adds that the same concept works for the public sector in an urban environment where agencies can geo-fence targeted areas in a city and provide real-time information via SMS text for people inside that polygon. If they are outside that zone you don’t get the message since the event doesn’t impact them.
“These are the types of approaches that are changing the way we communicate and protect people while helping them protect themselves in the public sector,” he adds.
About the author: Steve Lasky is the editorial/conference director of SecurityInfoWatch.com Security Media Group. His is also the Editor-in-Chief of Security Technology Executive magazine. He is a 30-year veteran of the security industry and a 27-year member of ASIS. He can be reached at [email protected].