Editor’s note: This is the 64th article in the “Real Words or Buzzwords?” series about how real words become empty words and stifle technology progress.
When I first heard the term Access Chaos, I thought it likely to be a marketing term of little practical use. Digging deeper, I learned that it is being used to describe a 50-year old situation: that physical access control privileges are less and less manageable as two things grow in size: the number of electronically controlled doors or gates, and the number of access cards or credential holders in the system.
Recently I heard one particular company’s story. They have 25,000 employees. Every year 2,000 individuals exit the company, 2,500 are hired to backfill empty positions or fill new ones, 800 change roles or working locations, 1,000 are added due to acquisitions, and another 500 leave due to subsidiary sell-offs. On average, 25% of all people records change every year. That’s 6,250 personnel changes.
They believe it likely that hundreds of their people have inappropriate access resulting from a variety of human mistakes, many of which are bound to relate to critical asset areas.
Any of the access privilege errors can result in multiple access violations. But because the changes are ongoing, they don’t have any practical way of knowing where the errors are.
Furthermore, some percentage of the access privilege errors are cumulative, meaning that they are not solved by people leaving the company. Thus, incorrect access liability grows each year, and the organization is increasingly subject to the very threats the access control system was designed to prevent.
This is the situation that RightCrowd (www.RightCrowd.com) has accurately labeled “Access Chaos.” Per my own observations over the years, it exists with most employee populations that have over 1,000 access privilege holders. The larger the employee population, the greater the number of cardholders with unintended access privileges to critical asset areas.
In addition to access errors within the access control system itself, there are also other access control factors that are managed manually, and often serious corporate liabilities exist because of human errors in their management. Two of them are insurance and training requirements.
For personnel safety and other reasons, access to hazardous operations areas require individual safety training. Additionally, contractors working on site often have insurance coverage requirements. A serious or fatal on-the-job accident caused by an untrained person or to an uninsured person can result a multi-million-dollar settlement, not to mention the business interruption and the demoralizing effect on workers in the operations area.
Fortune 500 Companies
Only a small percentage of Fortune 500 companies have company-wide identity management systems and dedicated people who perform oversight on the access chaos factors. But most large business organizations just can’t dedicate personnel to the task and aren’t really aware of their true risks involved.
But this has always been the case. So why create the label now?
Access Analytics
RightCrowd has introduced a new cloud application that the company says, once and for all, lets you put an end to access chaos.
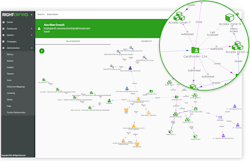
Called Access Analytics, it allows physical security, OT teams, IT, HR and business personnel to collaborate, review and take action to correct inappropriate physical or logical access to any assets and enterprise systems using a single graphical view that can present the access privilege information from multiple perspectives.
It can answer simple questions like, “Whose safety training is expiring within the next 30 days?” Access Analytics can initiate a notification to the individuals who need to redo their training, the people who manage their access privileges, and the supervisors who may need to help facilitate the time off work for training.
Why hasn’t anyone done this before? Well, it simply wasn’t possible using the database technologies that have been available – until now.
Access Analytics is a lightweight software that works with daily input feeds, typically a simple CSV file exported from the systems with access privilege information.
It puts the data into a graph database, a new type of database that can be used to store information about people and assets and the requirements and relationships that relate to them. A graph database is a special kind of database built to hold and navigate billions of relationships and query them with millisecond latency.
The Profium website describes the two following graph database use cases.
How is it possible that LinkedIn can show all your 1st-, 2nd-, and 3rd-degree connections, and the mutual contacts with your 2nd level contacts, all in real-time? It’s because LinkedIn organizes its entire contact network of 660+ million users using a graph database. Netflix uses a graph database for its Digital Asset Management (DAM) because it is a perfect way to track which movies (assets) each viewer has already watched, and which movies they are allowed to watch (access management). Note also that Identity and Access Management (IAM) has an essential role in DAM.
Traditional physical security systems rely on relational databases for their data storage. Relational databases aren’t designed to manage the scale and complexity required for the kinds of multi-faceted access control that large organizations need.
The graph database, plus RightCrowd’s patented way of using it, is what makes the performance of Access Analytics possible.
Access Analytics works with any access privilege management software, including traditional physical access control systems, Microsoft Active Directory, visitor management systems, parking access management systems, physical lock and key management software, HR systems, learning management systems and so on. It works for physical card credentials of all types, as well as mobile device digital credentials. The application is future-proof in the sense that it can work with all the systems and credentials in place now, plus those that will be adopted in the future.
You can also include logical access as well. For example, people who have access to a physical security system VPN.
Using Access Analytics
Access Analytics is a tool that uses your existing access management roles, responsibilities, processes and procedures to correct access privilege errors.
It does this by providing notifications to the access decision-makers, who can use the Access Analytics main view (see Figure 1) to see the full context for the recommendation, if needed.
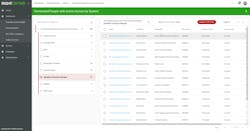
Often there is no need to consult the full view, because the rationale behind the recommendation is obvious, such as to remove a cardholder because the person’s employment was terminated, as shown in Figure 2.
There are no automatic access changes made to any access control systems or databases, thus it is a very low-risk deployment.
It is also future proof, because when an organization adds or removes a system containing access privilege information, it only requires a new CSV file data feed to be created for the addition and a simple configuration change in Access Analytics that can be made by an authorized Access Analytics user. (There are other data feed types available. The CSV file is the simplest one and is most commonly used.)
Self-Paced Adoption
Access Analytics can be deployed one site at a time, beginning with the highest-headcount sites (the highest risk of access privilege errors) and move on from there. It establishes immediate visibility into the current state of access privileges, which can be viewed by facility, access control system, or privilege holders.
It can also consider the future state, such as access privilege requirements that are about to expire, as exist for licenses, insurance, training and certifications.
Rules
An important feature of Access Analytics is its use of rules. Access Analytics provides a set of default rules, for example, that terminated people should not have access privileges. Users can add custom rules, defining, for instance, that people on a leave of absence should have their access privileges suspended.
Once a few sites or access control systems have been enrolled in Access Analytics, and any important custom rules have been established, enrollment of additional sites can be accomplished in sequence or in parallel – at whatever pace is non-burdensome.
Auditability
A key shortcoming of physical access control systems has been the lack of auditability regarding access privileges. Even for companies who have very specific access control policies and procedures for physical access management, auditing conformance to those requirements has not been possible.
Additionally, Access Analytics eliminates manual access management processes as single points of failure in access management. Incorporating it as part of the physical access control system deployment provides daily automated assurance against manual errors and process incomplete workflows (such as can happen with vacations, transfers, travel, etc.).
Physical Access Control System Upgrades
Many companies are currently considering upgrading multiple disparate physical access control systems to standardize on a single access management software product. Sometimes that upgrade is software-based, such as for deployments bases on Mercury Security hardware, and sometimes it involves hardware as well.
Any such deployment project can be simplified by performing access-privilege cleanup prior to performing the upgrade. Historically, some companies have decided to fix their access chaos problem by re-credentialing all individuals and starting from scratch with the assignment of access privileges. That approach is highly disruptive, always takes longer than estimated, and doesn’t keep access chaos from creeping in again, which is what always happens.
Other companies have simply exported the cardholder and privilege data from their existing access control systems and imported it into the new system. This preserves the access chaos without providing a means to correct it.
Companies take this approach when they don’t realize the full extent of their access chaos, and wrongly assume that somehow the new system will let them manage access privileges better.
Using Access Analytics to resolving the access chaos problem prior to large-scale upgrades will lower the cost and shorten the timeframe of the upgrade. It will enable progressive upgrades at any pace that makes sense, and ensure that access privileges are always correct throughout the upgrade.
There will be no “limbo” state for access privileges where no one is sure where access privileges stand until the upgrade is complete. This can be critically important for organizations with regulatory requirements relating to physical access control.
Knowing vs. Assuming
For the first time in the history of physical access control, it’s possible to know the exact state of access privileges. This writer has been involved in several dozen large-scale access control upgrade projects. In every case, the state of access control privileges was always much worse than anyone had thought. Unravelling the mess always impacted project execution time.
This article is not a full description of the Access Analytics product. It has only scratched the surface about its features and the extent of its application. The main points are these. For the first time in the 50-year history of physical access control systems, physical access privileges can be managed fully and accurately, and in a non-burdensome way – for any sizeable access control system deployment, no matter how many brands of access control systems there are, and regardless of the number of sites. Until now, the technology did not exist (modern graph databases and cloud computing) that could handle the management of the complex factors involved in truly comprehensive access management.
There are other factors, such as the cyber strength of access credentials, tailgating, and the trend towards open-space building floor plans. However, addressing those factors is practically meaningless if there is no tight control on access privileges.
Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s Top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Follow Ray on Twitter: @RayBernardRBCS.