Technology Transformation and the Security Integration Business Model
When CapEx-based technology purchasing cycles are significantly longer than product life cycles, the CapEx-based project approach cannot keep customer products and systems technologically-current. That is one of the primary reasons why the “as a service” business model is gaining ground in nearly every industry. Subscribing to technology as a service helps ensure that technology can be kept current to the extent the customer requires.
Another reason that as-a-service offerings are growing in number is that the computational power and connectedness now available in the cloud cannot be feasibly established using on-premises equipment and systems. For these and other reasons, many security integrators’ customers are transitioning their business applications to the cloud. According to software-as-a-service (SaaS) management platform provider BetterCloud, by 2020, more than 50 percent of all surveyed SMB organizations expect to run 100 percent of their IT in the cloud. Cloud-based offerings, as such, by their very nature are subscription-based services.
We are now approaching the point in the security industry where as-a-service offerings will be able to provide significantly greater benefits than traditional security technology offerings. Such offerings are now under development at several companies, and some are already available. As the pace of technology advancement continues to increase, as-a-service offerings will become the primary way to provide customers with security operations capabilities that remain technologically-current.
A 2016 report from market research firm Technavio predicts that the global “security-as-a-service” market will grow steadily and will post revenue of nearly $1.5 billion by 2020.
The Realities of Cloud Adoption
One reason that security industry adoption of the cloud has not kept pace with business cloud adoption is that most business cloud applications are software-only offerings – meaning they do not require on-premises hardware infrastructure. Their computing hardware can be in the customer’s data center, or in the cloud; thus, cloud adoption is easier for business applications because customers are subscribing to software usage. They do not own the software or hardware, they just license its use.
In contrast, most security applications involve many on-premises devices whose purpose and function requires them to remain on-premise; hence, “cloud” applies only to the software server portion of the system – at least that is how it used to be. Today, on-premise security devices are not the same as they once were; they are now becoming increasingly more intelligent, with computing and network communications capabilities that legacy devices do not. More and more of these intelligent devices can connect to cloud systems, or have their data sent to cloud systems to be analyzed or better used.
That is already happening with modern video analytics, which now makes a virtual model of the camera’s field of view, and uses machine learning to distinguish meaningful objects and activity from the scene background. This data extraction can be performed on the camera. The virtual model elements of scenes, objects and activities – which are text data, not video images – can be easily sent to the cloud for advanced analytic processing, either straight from the camera or via on-premise video appliances. In the cloud, computing power can scale up or down instantaneously, as the processing of video scene data requires. Data can be correlated between cameras and matched with scene path data for object tracking and prediction.
It is reasonable to expect that subscribers to cloud analytics data processing would pay only for the computing and data storage resources their video scenes required. Cloud-based analytic systems can be continually updated as technology advances, and so customers can be provided with always-current technology and instantly-scaling computing power at a fraction of the cost it would take to establish and maintain such capabilities in their own data centers.
What we are seeing is that as technology advances, cloud-based security offerings can provide increasingly greater value than on-premises client-server systems. However, there is even more value to be obtained from sources that we are not thinking about yet – the new devices that are available for facilities today.
Intelligent Buildings
The facilities that we are protecting are not standing still technologically – at least not for long. The term “Human-Friendly Buildings” is being used to describe the goal for intelligent buildings, and security plays an integral part in that vision (see more at bit.ly/human-friendly-connected-buildings).
Here is an example of how our facilities are changing due to the intelligent building infrastructure: PoE-powered intelligent LED lighting fixtures – which save 60 to 80 percent on lighting electrical costs – are being installed in new and existing buildings. There is no high-voltage cable and conduit to run for this lighting, just network cable; thus, security systems can control the LED lighting via the building’s network. Lighting color can be set to red for evacuation, yellow for shelter in place or green for all-clear, for example, on a room-by-room basis. Lighting fixtures can use a sequence to indicate evacuation direction, or hallway lighting at unsafe rooms could have lighting flash red as a warning. Network cameras with two-way audio can be used to provide room and area-specific instructions and to get status reports from occupants, and the evacuation progress can be tracked in real-time with sensor and video information.
In another example, when occupancy sensors show that someone is working alone in an isolated section of a building, a security officer can perform a friendly foot patrol visit and let the occupant know that security is actively patrolling the building. This is a human-friendly element of making workplaces safe and secure.
Technology Transformation
The intelligent building is just one part of the Internet of Things growth, and the arrival of IoT means traditional security devices will soon be outnumbered by IoT devices; and the data from these devices will be used in real time by many applications, including security systems. Security systems infrastructure will include intelligent devices that are not “owned” by security, and some of that data will be available only through cloud services.
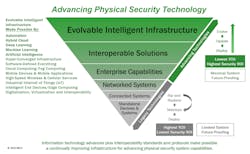
Now that so much of technology is interconnected and evolves significantly through software and firmware updates, we need to realize that the job of designing, deploying and maintaining electronic security systems is that of planning and building an evolvable intelligent system infrastructure – one that can be advanced as technology advances and be updated in accordance with a customer’s evolving risk picture, without having to replace entire systems.
This is a new concept, but when you grasp it you can see why physical-security-as-a-service (PSaaS) – a combination of hardware-as-a-service (HaaS) and software-as-a-service (SaaS) offerings – makes more sense than the 40-year-old approach we have been using for legacy technology.
Because the nature of the technology we provide is changing drastically, a fundamentally different security system design concept is needed, one that suits the nature of the growing and evolving technology infrastructure on which our security system applications will depend.
As the graphic above illustrates, electronic security technology began with mostly-analog systems, sold under the traditional sales model, and funded by customer capital expense projects. Under that approach, security systems are installed and immediately begin their transition from “new” to “outdated” and then to “obsolete.” Every so often, entire systems are ripped out and replaced, which is almost always a disruption. This worked when product life cycles were a decade or longer, and security technology was very slow to advance.
Now, we face increasingly rapid technology advancement, high-availability and high-capacity network connectivity, and the growing customer need to be technologically-current. The natural response to this situation is the transition to physical-security-as-a-service. That transition is supported by the fact that customer companies are generally transitioning to cloud-based offerings to remain technologically-current, to be connected to the growing number of important data sources, and to use technology services on an on-demand basis.
Integrators and consultants should start preparing to guide their security customers in aligning their security thinking, as well as their technology deployment practices, towards the as-a-service model. This will enable their customers to embrace emerging technologies of value to their security program, and obtain a higher security ROI for their organizations.
Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). Mr. Bernard is a Subject Matter Expert Faculty of the Security Executive Council (SEC) and an active member of the ASIS International member councils for Physical Security and IT Security.
Other Articles in this Series
This is the sixth article in Ray Bernard’s series dealing with cloud-based systems. Here are links to the other articles:
- Avoid Key Cloud Services Mistakes: www.SecurityInfoWatch.com/12177153
- Cloud Computing: Clarity or Confusion? www.SecurityInfoWatch.com/12211857
- Evaluating a Cloud-Based Service: www.SecurityInfoWatch.com/12223384
- Addressing Cloud Risk: www.SecurityInfoWatch.com/12243763
- Cloud Security Roles: www.SecurityInfoWatch.com/12270050