On the Scene at GSX: Organizations are migrating to advanced security management software for a proactive risk stance
If there’s confirmation that software for physical security systems and operations management now drives the strategic risk planning for enterprise-level organizations, you only should look at solutions providers such as Topo.ai. The company delivers flexible software solutions for assessing and responding to threat intelligence. As large organizations built out their visual command centers or GSOCs, critical-event management (CEM) software is critical for enhancing operational resilience seamless business operations.
I recently discussed how organizations can aggregate intelligence and asset information from any source for situational awareness and subsequently prioritize and coordinate their responses with Phil Harris, who is the CEO and founder of Topo.ai. The fact that AI-driven automation allows diverse industries to react with more precision and consistency when addressing high-risk events lets security and risk-management teams leverage the intuitive nature of these advanced software platforms.
Topo.ai will demonstrate their software solutions at the GSX event Sept. 12-14 in Atlanta in Booth 3654.
Steve Lasky: When we talk about enterprise-level organizations and even mid-size, what constitutes critical-event management given that it’s a term thrown about with not a lot of definition or understanding by most people? If you had to explain what critical-event management is as it pertains to the business organization, what would it be?
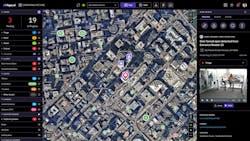
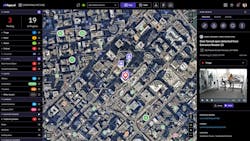
Phil Harris: It’s the ingestion of any and all risk events, internal and external, that might emerge as a threat to the organization. So, the consolidation of all internal and external risk events into a consolidated, consistent and compliant process that security operations can understand and address their risks are threats and then escalate them and respond accordingly is critical. We view it as how data moves. Organizations typically subscribe to intelligence feeds. They have a range of internal systems. Emerging from these systems are risk notifications. They can come in through email. They come in through a system dashboard. A critical-event management system brings all of that data together into one system, and it's run through a consistent and compliant process.
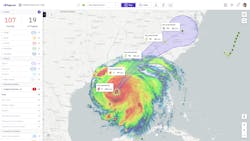
That process includes a mapping, and mapping is important, because it allows customers to perform situational awareness. If a risk is near a company asset, a fixed or mobile asset, an office, a traveler, security operations organizations have to quickly understand the proximity of the threat. If it isn’t nearby, it's probably not a threat to the organization. If it’s nearby and the severity of the risk is high, then the team might have to respond accordingly. Security operations is responsible for adjudicating basically emerging risks on a global basis to identify their threats. It’s an enormous mission.
The range of inputs of risk notifications is broad and wide. What we’ve noticed is that organizations run and identify these events in many different systems, which are siloed. They could be an email, and many times they go unacknowledged, or they sit in an inbox or a system for an extended period, and the organization is flat-footed. In a case like this, when the risk emerges as a threat, not only has security operations not acknowledged it, but they also are behind on their response.
The second part of the critical management system is to seamlessly communicate to people who can organize a response to that threat, so the organization isn’t affected. It’s a risk-mitigation activity that might involve people who are local on-site. It might involve notifying the people who are affected, such as the travelers in an area. A critical-event management system brings in all of the inputs on the risk-notification side, internal and external, and allows security operations to process them, identify whether they’re actual threats and then seamlessly and rapidly communicate those threats to people who are responsible for responding and mitigating them for the organization.
Harris: A common problem is a CEO calls a chief security officer and asks, “Did you hear about the bombing in Paris?” And the CSO might not know but calls their GSOC, which also doesn’t know about it. When they do a post-incident or post-event review, they find that they were notified an hour and a half earlier, and that alert was sitting in someone's inbox. Unfortunately, perhaps it had a severe effect on the company. So, getting caught flat-footed on a major event is a common occurrence. Implementing a system, such as TopoONE, allows you to run everything through one system.
If there’s a lack of response to system notifications, it can nudge operators, letting them know a severe alert just came in: Jump on it. We’re a cloud-based platform, so in the new world, if the CEO is a news junkie, they’re on top of events more than anyone else. In the new world, the CEO would call the CSO. And if they had a critical-event management platform such as Topo and asked, “Did you hear about the Paris bombing?” The individual can say, “No, I haven’t heard, but hold on a second. Just give me a moment” and pull the news up on their device or on their machine from a dashboard that lists the events that the GSOC is working.
The team would be working the event if they got that intel from an alert feed or some other feed and will know the status. They immediately would relay that they are on it and that they got notified by their intelligence provider 22 minutes ago. Instantaneously, they would know 16 travelers are within 10 miles of that location and it’s within 8 miles of their Paris headquarters. The team already would have initiated a response protocol based on the organization’s business continuity plans and will keep management updated as the situation evolves. That’s the new model where it’s data transparency, response transparency and then teams working compliant processes, so things don’t fall through the cracks.
Lasky: A couple of the big issues that face enterprise-level organizations still are being driven by the pandemic and the fact our workforces are spread out. You’re looking at staffing shortages across the board. You’re looking at budget issues and the constant battle security endures on to show return on investment to the C-suite. So, talk to me about how a software platform that handles event management is able to answer the questions of staffing shortages and budget and also demonstrates ROI.
Most of our customers have a significant work-from-home workforce, and the duty of care has extended beyond just office locations. One of our customers has close to 50,000 employees. There’s an emerging sense of responsibility that we should monitor risks in and around those workers’ homes, because it’s their office now, right? That’s increasing the mandate.
Our mission at Topo isn’t just helping with that individual event, but also looking at all of the events and all of the risks to unlock the data and insights security leaders require to improve their operations and build a more resilient organization. That’s a pretty big mandate — to unlock the data and insights security leaders want. But they can’t do it unless you bring all that data together. And if you don’t bring all that data together through one critical-event management platform that’s extensible and cloud-based, there’s no way of truly unlocking it through reports and dashboards that leaders demand to make strategic decisions.
Lasky: I realize one of the goals with your solution — because you feature an open-architecture and cloud-based platform, is trying to include as many partners as possible to benefit your clients’ demands. You’ve been highly active with aligned technology companies that you’ve brought into the solution. What’s your strategy on working with other technologies and risk-solution companies to help your clients to maximize their solutions?
Harris: Great question. We have a client-first approach, and we take all comers. We integrate with any risk-notification provider, any adjacent system, whether it’s an ERP system or a physical security camera or access control system — any intelligence feed. We are truly open. What we see in our space though, is we have a handful of vendors that try to force their own end-to-end solution and aren’t open. Closed systems aren’t the way modern software within an enterprise environment is adopted and built. I don’t believe that it keeps the customer first. Because if the customer wants to bring in a certain intelligence feed but wants to standardize on a system such as a Topo, not supporting those best practices for that end user is shortsighted and tends to muscle the customers into a place that makes them unhappy.
We’ve taken a different approach. We’re like Switzerland: We play with everybody but always with the customer in mind. How can we help the customer ingest any and all risk-event data on the one side and then connect to any adjacent system to communicate and manage the response on the other side? It’s a unique strategy in our space.
About the Author
Steve Lasky
Editorial Director, Editor-in-Chief/Security Technology Executive
Steve Lasky is Editorial Director of the Endeavor Business Media Security Group, which includes SecurityInfoWatch.com, as well as Security Business, Security Technology Executive, and Locksmith Ledger magazines. He is also the host of the SecurityDNA podcast series. Reach him at [email protected].