Understanding and protecting your attack surface from cyber threats
One of the biggest challenges for cybersecurity defenders is keeping track of their potential attack surface as it grows and evolves. This means discovering, analyzing, and remediating cybersecurity vulnerabilities before they can turn into major incidents. Security teams are tasked with defending a broader, more dynamic environment and an expanded set of attack surfaces.
This expansion is due to a variety of trends, including the growth in cloud-native computing, the integration of the Internet of Things (IoT) into corporate networks, the popularity of daily software builds, and the use of complex software supply chains. All of these have made obsolete the days when IT security managers could claim their attack surfaces were static and easily trackable. This complexity means added risk, a higher potential for costly security breaches, and an added burden for defenders to anticipate and prevent these attacks.
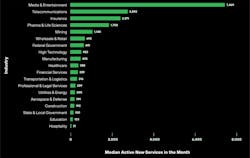
A recent research report from Palo Alto Networks’ Unit 42 shows new trends in this arena and is based on observations collected during 2023 from 265 global enterprises. The report found that, on average, an organization adds over 300 new cloud services every month. But that average is deceptive because there is a wide variation in specific circumstances, with organizations from industries such as media and telecommunication that added thousands of new monthly services.
The issue is that attackers understand these new dynamics and have developed tools to automatically scan the global public cloud infrastructure in mere minutes to look for their hacking opportunities. That speed is alarming because it is coupled with a quick response time; many of these scans also happen within minutes following vulnerability announcements. Half of these observed exposures happen with remote access services (such as RDP and SSH) or across IT and security infrastructure products and protocols (such as NetBIOS and SNMP).
Even though the attack methods themselves aren't new, the way they're combined—starting with initial breaches through these services to quickly steal data and insert malware—keeps evolving and improving.
Practical strategies to protect your organization
While the balance of power continues to be in favor of attackers, who are faster and getting better at finding vulnerabilities than defenders are at securing them, there are proven approaches that can help tip the scale in favor of security teams. Here are some practical suggestions on how to reduce your attack surface.
Maintain persistent, comprehensive visibility of all internet-exposed services
Strategies to identify and respond to attack surface risks start with continuous, comprehensive scans of your organization's ports, services, and devices, along with ensuring updates to affected protocols and applications. Many organizations still perform these checks on their infrastructure quarterly or less frequently. Continuous monitoring is key to effective attack surface management and receiving timely notifications when something is detected.
Remediate critical exposure risks in real time
Detection is only half of the battle. It is crucial to have processes and technologies to assist security teams in identifying, communicating, tracking, and automating remediation where possible. Adversaries are at work constantly, so security teams must be operating at the same cadence. Because many exploits happen within moments of a new vulnerability announcement, defenders must eliminate any delay in deploying these updates across their corporate networks.
Monitor for unsanctioned services or shadow IT
Organizations should regularly check perimeter resources to distinguish between expected assets and unknown or out-of-scope ones, ensuring adherence to security baselines. Deviations from these baselines are often the most vulnerable to compromise, making them prime targets for attackers.
Stay current with changes to public internet resources
Another strategy is to fine-tune security policies to eliminate potential threats and keep current with patches and other system updates to harden these resources. SaaS and cloud applications are being updated frequently, which means threats could occur with unintentional vulnerabilities introduced in a new version.
Accepting the new rules of attack surface management will take some effort to change well-worn security practices. But the time to change is right now, before the next breach happens.
About the Author

Greg Heon
Dr. Gregory Heon is a Sr Director of Product Management at Palo Alto Networks, where he leads the product management function for Cortex Xpanse. He has been a part of the Xpanse team for nearly 8 years and holds a PhD from Stanford University in Management Science & Engineering.