As organizations have become more mobile and geographically dispersed, the traditional centralized Wide Area Networking (WAN) model that once served them so well has started to break down. The remote user - once the exception - has increasingly become the norm, with many working from smaller branch offices across several time zones, from home, or while on the move.
Amplifying this business decentralization has been the move to software as a service (SaaS) offerings such as Office 365 and the migration of applications to cloud service platforms including Amazon AWS and Microsoft Azure. These SaaS offerings turn software, storage and computing resources into a service that exists on servers beyond the traditional network perimeter.This has created challenges for teams tasked with optimizing, managing and protecting the infrastructure. Although traditional firewalls protect against traffic flowing into the data center or other physical locations, they cannot provide visibility or security for remote users that connect directly to the Internet or cloud-based resources.
SWG Development
Secure Web Gateways (SWGs) have emerged to address these issues and accelerate digital transformation as companies move workloads and applications to the cloud. Essentially, these allow a mobile and remote workforce to access the internet directly without having to route traffic via data centers, giving security teams the ability to perform basic tasks such as URL filtering and to protect their users against web-based threats. They can also perform additional important security tasks, such as HTTPS (encrypted) traffic inspection, and in some cases, data loss prevention (DLP), cloud access security broker (CASB) functions, or even implement protections against zero-day attacks using sandboxing technology.
Because the nature of the technology invites comparisons with traditional anti-virus software on endpoints, as well as security devices such as stateful or next-generation firewalls (NGFW) and intrusion prevention systems (IPS), buyers can become confused about whether SWGs are intended to be complimentary or act as a replacement. To address these questions, we first need to examine the pressures that have helped shape the evolution of SWGs and put their emergence and use cases into context.
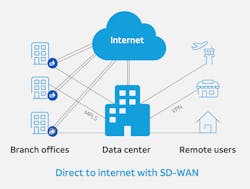
The Acceleration of SD-WAN
A modern approach called Software-Defined Wide Area Network (SD-WAN) utilizes an architecture that turns different types of WAN connectivity into a single virtual entity to offer a wide range of benefits. With SD-WAN, organizations can augment their MPLS lines with less expensive commodity internet such as broadband, fiber, and LTE, allowing the organization to quickly add additional bandwidth at a lower cost than if the organization were to implement additional dedicated circuits. Having multiple network links that are supported by different technologies is also an investment in network resiliency and business continuity. If inclement weather or a construction crew were to sever one of the network links, SD-WAN can route traffic virtually seamlessly to the viable circuits until service is restored.
But deploying SD-WAN in order to connect branch and remote users directly to the internet does have some repercussions, most notably for security. In the legacy hub-and-spoke architecture, there was one way in and one way out of the network. But with the new model, there are now many network breakouts, sometimes even hundreds or thousands across a wide geographical area. Each of these connections to the internet represents an avenue for attack, and therefore, security measures must be implemented.
Fortifying Security Practices
Cloud-based SWGs offer administrators a way of applying unified security policies across their users, virtually anywhere that they conduct business and provide centralized visibility, allowing administrators to remain informed about what activities are taking place on their network. Together with SD-WAN, this overcomes the traditional setback that users suffer lower performance and weaker security simply because they are farther from the network’s core. SWGs protect users against web-based threats by restricting what content can be accessed. They also offer a solution for organizations to perform a granular inspection of encrypted web traffic for network management purposes with minimal effect on network performance. A cloud-based architecture scales more easily because capacity can be added without the need to buy expensive security equipment as businesses expand, whether that be adding new offices, integrating company acquisitions, or conducting mergers.
In time, many organizations find that SWGs can replace elements of their current security infrastructure such as SSL/TLS inspection appliances, intrusion prevention systems (IPS), and firewalls for some branch office locations. In some instances, SWGs may have overlapping capabilities with other technologies but should be understood as complementary rather than as a direct replacement. For example, although SWGs can perform web filtering and deep-packet inspection, and protect against web-based malware, they are not intended to replace endpoint security. They should also not be confused with web application firewalls (WAFs) which are designed specifically to highly protect web servers from external attacks, such as Distributed-Denial-of-Service (DDoS) floods.
In today’s digital business environment, businesses have become more decentralized and mobile to fulfill business objectives and remain competitive. This has given rise to a new type of virtualized WAN in which the data center is a resource but no longer the center of the network. Although many networks still retain elements of this legacy architecture, the future belongs to flatter, more dynamic and adaptable topologies that prioritize employee productivity over technological hierarchy. SWGs and SD-WAN are complementary elements that can help organizations modernize their network and security so they can scale to support the new initiatives.
About the Author:
Mary Blackowiak is a Lead Product Marketing Manager for the network security portfolio with AT&T Cybersecurity. She has over a decade of B2B marketing experience in the high-tech space including positions with Forcepoint, NSS Labs, and Best Buy for Business.