Study finds troubling perception gap in data breach awareness and coverage
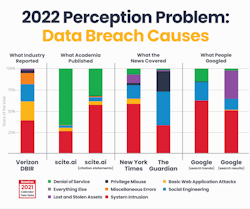
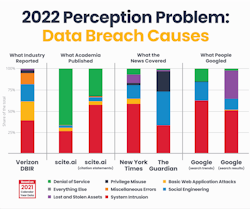
RICHMOND, Va. – A recent study published by Hive Systems found that media, academia and the general public vastly overestimate the prevalence and susceptibility of system intrusions while underestimating more common means for data breaches. A comprehensive analysis of academic publications, media trends, and search engine results showed that while system intrusions account for only one-third of data breaches, more than two-thirds of coverage and searches on data breaches focused on the topic.
“Having more accurate conversations about cybersecurity threats is critical,” said Alex Nette, Hive Systems CEO and Co-Founder. “If we’re focused on what we see in the news and online, it creates a bias that leads to cybersecurity investments in areas that may not reduce risks for your company.”
While the industry-standard 2022 Verizon Data Breach Investigation Report (DBIR) listed system intrusions as the most prevalent cause of data breaches (39%), the public perception far outweighs its pervasiveness. According to the report, not only were internet searches for system intrusions nearly twice as common (62%), the second-most common tool for data breaches – basic web application attacks – was barely explored (<1%).Similarly, media coverage predominantly focused on system intrusions and social engineering – approximately 75% of all coverage. That amount of coverage equates to almost 30% more than its frequency as reported by the DBIR. While The New York Times dedicated a majority of its coverage of data breaches to system intrusions (58%), The Guardian spent 44% of its coverage on social engineering – a stark difference in coverage between the two outlets.
On the academic side, almost three-quarters of all academic journals published focused on denial of services – a topic that accounted for a minuscule 1% of total data breaches.
DBIR incident and breach classification patterns are based on the clustering of data as opposed to how the cybersecurity industry tends to group them. Types of breaches include System Intrusion (e.g., ransomware, malware, stolen credentials), Social Engineering (e.g., phishing emails, texts, phone calls), Basic Web Application Attacks (e.g., SQL injection), Miscellaneous Errors (e.g., misconfigurations), Privilege Misuse (e.g., disgruntled employee data leak), Lost and Stolen Assets (e.g., a stolen laptop or phone), Denial of Service (e.g., DDoS attacks) and Everything Else (e.g., ATM card skimmers). The report noted that after system intrusions, the most common methods of data breaches were basic web application attacks (23%) and social engineering (21%).
The graphic of the research results is available for download here.
About Hive Systems
Hive Systems provides smarter cybersecurity solutions with our trusted experts. Leveraging our collective experience, we promote a true partnership by understanding what makes your organization unique to help evaluate your cybersecurity strengths and vulnerabilities. Together, we’ll develop a risk reduction strategy that best utilizes your existing investments, including both technology and people, to reduce your risk anywhere - so you can keep your information secure everywhere. Through Hive Helps, we offer pro bono consulting services to qualified non-profit organizations and communities to ensure that limited resources don’t hinder social progress.