Risk management is not about eliminating risk but managing it and being prepared to deal with security failures through resiliency. A site security survey and a vulnerability/impact/risk matrix can help integrators aid customers in reaching better business decisions relative to existing and new security video technology. After all, there is a diversity of potential security threats, including accidents involving employees and visitors, natural disasters, data loss, fraud, intellectual espionage, vandalism, threats to people, physical theft and brand and reputation attacks.
Many security operations already collect a myriad of data related to security incidents as well as link the data to specific security programs. They report and log:
- Number of security incidents in the past 12 months
- Types of security incidents
- Primary methods used in security incidents
- Likely sources of security incidents
- Security incidents' impact on the organization
- Estimated individual and total financial losses as a result of security incidents
- Manner in which the organization learned of security incidents
- Total downtime over the past 12 months as a result of security event
Depending on what comes out of the site security survey and then is applied to the vulnerability/impact/risk matrix, there may be the need and justification for spending on additional products and services.
Track what needs to be done
A site survey can make it easier to see exactly what needs to be done to control access and surveillance within and outside a facility. The survey provides a way to obtain answers and plan a course of action. Often, by focusing on the right actions, an enterprise can make major improvements at a cost lower than expected. A site survey will find out what is right and what is wrong with a facility's perimeter and internal physical security, including electronic access control, intrusion detection and security video.
One survey benefit is identifying security gaps. Without looking at the overall picture, security can fall into the trap of short-term fixes such as repairing an individual door that doesn't close properly or throwing up a camera based on increases of vandalism in a section of a parking lot. Putting out these fires may not do much to improve overall security nor help with a master plan of growing security systems in the right ways. A good survey will spot six elements:
Description of the facility or campus. Articulate a clear and concise understanding of the purpose of each facility and its integration to other buildings. The ability to secure a facility depends in large part on its function.
Existing systems. A comprehensive survey should note the location of every security component, such as card readers, cameras and intrusion detection devices.
Communications infrastructure. In these days of IP-based security systems, a comprehensive site survey should document the configuration, availability and capacity of existing communications networks. IT must play a survey role.
Regulatory requirements. In some instances, a site survey lets the security team compare the existing security program against regulatory and compliance requirements.
Power availability. The access and security video camera points surveyed need power. In addition, remote locations and new locations have power needs, too.
Site preparation. The survey team also should look for conditions that may impede or preclude the effective use of an electronic security system.
With that information written down, a survey tour will be more efficient. Armed with a clipboard of survey forms and digital camera, walk outside and around the various building perimeters to get a better understanding of how the enterprise is laid out from a security perspective. Think of it is an onion with an outer layer and inner layers leading into the center or multiple centers with the most important assets protected.
Make sure to number and photograph vehicle and people entrances. This will be useful in developing later recommendations or in making changes of security camera locations and their views. Grade each access and security video point.
- "A" is for those functioning properly.
- "B" functions properly but has cosmetic issues.
- "C" is for doors and cameras that require maintenance or changes in positioning.
- "D" indicates that a defective or ineffective item needs to be replaced or upgraded.
- "F" indicates a need for a camera or, in the case of door controls, a code violation, which will require a new installation or product replacement.
Put matrix numbers to the test
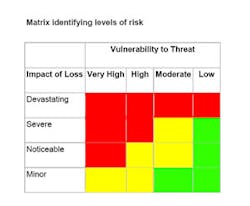
The next step of the site security survey is appreciating the threats and vulnerabilities associated with the site. Different than a site security survey, a threat assessment considers the full spectrum of threats (i.e., natural, man-made, accidental) for a facility, location or camera point. The assessment adds supporting information to evaluate the likelihood of occurrence for each threat and how vulnerable the site is (see chart to left).
Post the general threats previously identified:
- Accidents involving employees and visitors
- Natural disasters
- Data loss
- Fraud
- Intellectual espionage
- Vandalism
- Threats to people
- Physical theft
- Brand and reputation attacks
Then, rank the potential impact on the business for each. Impact of loss is the degree to which the mission of the business is impaired by a successful attack from the given threat. A key component of the vulnerability assessment is properly defining the ratings for impact of loss and vulnerability.
Devastating: The facility or the enterprise's reputation is damaged or contaminated beyond near-term use or value. Most items or assets are lost, destroyed or damaged beyond repair and restoration. A violent incident may close the facility or a crucial part of it for a significant number of days. The number of visitors to the facility and others in the organization may be reduced by up to 75 percent for a period of time. An example would be an earthquake.
Severe: The facility or the enterprise's reputation is partially damaged or contaminated. Examples include partial structure breach resulting in weather/water or a severe criminal incident, smoke, workplace violence, major fraud or fire damage to some areas. Some items or assets in the facility are damaged beyond repair but the facility remains mostly intact. The entire facility may be closed for a shorter period of time. The number of visitors to the facility and others in the organization may be reduced by up to 50 percent for a limited period of time. An example is a workplace violence incident that includes multiple loss of life and national media coverage.
Noticeable: The facility is temporarily closed or unable to operate but can continue without an interruption of more than one day. A limited number of assets may be damaged but the majority of the facility is not affected. The number of visitors to the facility and others in the organization may be reduced by up to 25 percent for a limited period of time. Air conditioning was disabled.
Minor: The facility experiences no significant impact on operations (downtime is less than four hours) and there is no loss of major assets. The parking garage wall suffers graffiti. Vulnerability is often a combination of the attractiveness of a facility as a target and the level of deterrence or defense provided by existing counter-measures that can include policies, procedures, products and services. Target attractiveness is a measure of the asset, reputation or facility in the eyes of an aggressor and is influenced by the function and/or symbolic importance of the facility. Sample definitions for vulnerability ratings include very high, high, moderate and low.
A combination of the impact of loss rating and the vulnerability rating can be used to evaluate the potential risk to the facility from a given threat. A vulnerability/impact/risk matrix can display overall elements or drill down to specific locations such as the perimeter, parking garage, entrance and exit doors, hallways, computer center and security command and control. Indeed, there is a need to fill in the matrix based on specific threats linked to specific locations and their existing security measures.
The overall assessment
There are numerous practical outcomes of the overall exercise. For instance, is the parking lot in an urban neighborhood? Have there been escalating numbers of incidents of vandalism and trespassing that the CEO and workers have all mentioned? Are employees feeling less secure when using the lot? Has local law enforcement recently requested more detailed security video of incidents? If so, place this area in the severe impact on loss and high vulnerability to threats on the matrix.
Thanks to a site security survey and vulnerability/impact/risk matrix, integrators have the data to more accurately assess their customer's operation overall and in detail as well as use the exercise to both justify purchases to the customer and their bosses.
About the Author
Mark Wilson
vice president of Marketing, Infinova
Mark S. Wilson is vice president of Marketing, Infinova, Monmouth Junction, N.J. ?