One of the side effects of security technology convergence (information technology being integrated into electronic security systems) is that it tends to focus attention more heavily on technology than on the people and processes of security. This has led to an ironic situation where one of the most beneficial uses of information technology - one that is actively being realized in other departments of the business - is being overlooked by security departments: the use of information technology to manage and improve business processes.
Automation, Workflows and Processes
We in the security profession (security practitioners) and the security industry (product and service providers) are still thinking in terms of automating security actions at the task level, through use of modern-day security systems, mostly for incident response. While this is beneficial, it is a limited application of information technology. A broader application would be to use technology for workflow automation.
Workflow automation and office automation are decade-old terms that were commonly used when many businesses were computerizing paper-based tasks, in the late 1980s and early '90s. The term automation was coined in the late '40s and is a shortened form of automatic operation. After the advent of computer systems, automation came to mean replacing paper-based work with computer-based work.
A workflow is a set of actions that are part of an overall business process. For example, visitor management typically contains several workflows: visitor registration (which typically includes visitor sign-in and visitor's badge or pass issuance), visitor notification (to the person being visited), and visitor exit (sign-out and return of visitor's badge).
Tasks and Procedures
Historically, physical security administration and operations processes in most organizations have not been considered business processes. In the earlier days when the security officer function consisted mainly of manning a post at a building entrance or exit, the job consisted of performing "tasks" that were assigned and enforcing "procedures" to be followed, and that terminology has largely remained in use.
In the meantime, outside of the security department, the term workflow management came to represent the manager's perspective, as businesses expanded their use of information technology and systems to improve the management of work being done. The workflow management perspective gave rise to the business process perspective, and the term business process management (or BPM) was developed to express the focus on business process improvement. Many companies developed business process management systems (BPMS), which incorporated standards developed at several levels - including Business Process Execution Language (BPEL), the language that information system computers use to exchange process execution information.
What does all this have to do with security? Plenty. The newness of this terminology to security practitioners is evidenced by the fact that practitioners have been missing out on standard business tools that other departments are using to run their portions of the business effectively and efficiently. That no longer needs to be the case.
Tools for defining and managing security business processes - and integrating them into related non-security business processes - are being deployed by the security departments of companies like Symantec and Cisco. Automation in security systems used to be confined to automating alarm responses. Workflow automation is now being extended to security administrative work, including for security workflows that are part of larger business processes such as employee hiring and termination - or on-boarding and off-boarding, as they have come to be called.
Workflow Orchestration
Designing the interaction between departmental business processes is often referred to in the IT world as "orchestration" rather than "automation," because the primary task is to arrange how the various departmental processes will work together.
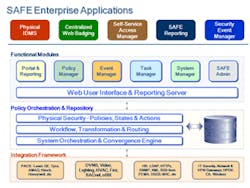
One product for implementing physical security workflows that involve multiple systems is SAFE by Quantum Secure (www.QuantumSecure.com), which is actually a suite of applications. Some of the system's functions are illustrated in Figure 1. SAFE can work with multiple brands of access control systems and other security systems to provide a single point of identity management and event management for all physical security systems. The system integrates with Human Resources (HR) and other corporate information systems to integrate security workflows with non-security business processes.
The term "orchestration" is used in Figure 1 to refer to the role of SAFE's rules-based engine in managing workflows. For example, the HR Department's candidate approval workflow would invoke the security department's background check workflow, and the results of that background check would determine whether the candidate is accepted or rejected for employment. If approved by Security and HR, the security department's new employee training schedule workflow would be invoked to enroll the new hire in the training program and update the visitor management system's roster. The trainee physical access assignment workflow would create the appropriate record in the access control system database, and the security badge issuance workflow would create a task for the badge issuance officer's task list. Upon completion of the training class, the training supervisor enters the pass/fail status of each trainee, and the system would one again activate appropriate workflows.
Self Service
Using computers and information systems to implement security processes in a self-service manner can be valuable. For one thing, it can enable security functions to be extended more broadly using information systems, where extending them using human interaction would be cost-prohibitive. Visitor registration, parking permits application and access control privilege change requests are all processes that can be implemented as self-service items.
The Baxter Cherry Hill pharmaceutical manufacturing facility has implemented self-service access privilege changes using SAFE in support of its "lean manufacturing" initiative. Says Derrick Wright, security manager for the facility: "Lean manufacturing is about reducing waste - including wasted time - and adding value. Why not reduce waste and add value in security operations?"
The Baxter facility had a paper-based access control privilege change process that required employees to obtain permission signatures for a form. Depending on the availability of the approvals needed, this could involve considerble time and walking significant distances. The company's new process uses SAFE to provide self-service so that employees can initiate the access change request using kiosks. Approval requests are automatically presented as a task to the approving supervisors and managers, and the system manages the workflow and the overall time for full approval.
"We have eliminated the lost productivity time where the employee had to walk around for approvals," Wright says. "We have also reduced the administrative time required for security personnel, since once all approvals are in place, SAFE automatically makes the changes in our access control system. As part of that process, the system enforces our access control policies in accordance with our FDA and DEA compliance program."
Physical and Logical Security Bridge
In the U.S. government sector, the FIPS-201 standard now requires that physical access control systems obtain specific cardholder information from an identity management system that is common to both physical and logical security.
In response to the FIPS-201 requirements, Honeywell Intl. Inc. has partnered with Novell Systems to address the identity management system requirement. The partnership has yielded the Honeywell SmartPlus application suite, depicted in Figure 2. SmartPlus is powered by the Novell Identity Manager, which provides a workflow management engine. The product provides the ability to automate day-to-day tasks through its workflow engine, and can also provide real-time monitoring and enforcement of security policies.
Although Quantum Secure and Honeywell do not strongly promote the workflow capabilities of their products yet, the products have tremendous potential for increasing the productivity and quality of security administration and operations - including through the integration of security processes with business processes using the workflow integration capabilities.
Rules Engines
A rules engine is a software module that can apply predefined rules to information system events in real-time. When the rules engine is applied for workflow management, it is often called a "workflow engine;" when it is used for policy application and enforcement, it is called a "policy engine" or similar name; and when it is applied for situation management and event response, it is called a "rules engine."
Both SAFE and SmartPlus provide significant event management, compliance monitoring and policy enforcement functionality through their workflow automation capabilities. They apply to HIPAA, Sarbanes-Oxley, HSPD-12 and FIPS-201, and other security regulatory requirements, as well as to an organization's own security policies.
IPSecurityCenter from CNL (www.cnl.com) is another product containing a policy engine with compliance and policy management related features. IPSecurityCenter acts as a central application for managing multiple brands of physical security systems (access, video, alarm monitoring and building controls systems). Both access privilege management and event management capabilities are included in the product. Its workflow automation can be triggered by events in any system.
Real-Time Security Decision-Making at Cisco
Information and workflow management for situation evaluation and response is critical to Cisco's security operations - where technology is deployed to maximize Cisco's ability to respond. The concept for Cisco's security technology deployment is shown in Figure 3.
Critical events at Cisco facilities are reported by access control systems, video surveillance systems and building controls systems. Situational awareness is provided by a system that monitors and reports on news, weather and environmental situations that have the potential to impact Cisco facilities. Security personnel respond from the Security Operations Center (SOC), and if the situation warrants it, the Emergency Operations Center (EOC) is activated by management personnel to make strategic decisions, such as whether or not to shut down a plant and begin manufacturing of that plant's products at another facility.
Cisco's Policy Correlation Engine, developed internally, is a rules engine that is applied to critical event information from multiple systems globally, and can take a wide variety of actions - including activating call lists for specific message distribution, managing digital signage to display security messages and paging systems for broadcasting important information and instructions.
Cisco's deployment provides actionable information for situation management at all levels where it is needed: operational, tactical and strategic. This type of real-time security risk management is much more advanced and more valuable to the organization than the simple alarm response automation found in the systems of the '80s and '90s.
More Security Using Fewer Resources
Rules-based engines can aggregate information, and they can apply rules to that aggregation to identify situations in advance of when typical security procedures would bring the situation to light. Rules can be used to apply risk information to real-time operations, and they can also be used to reduce or quickly increase the level of security officer involvement based on risk.
One organization did a study of their "door forced open" alarms using recorded video. They discovered that if the alarm condition lasted 20 seconds or less, there had not been a security incident. They also learned that if the "door open" condition lasted four minutes or more, there was always a security violation involved. Applying this knowledge, they set up their rules engine to not report door forced open alarms unless the alarm condition persisted for more than 20 seconds. After 20 seconds an alarm condition was enacted and the corresponding video view would be displayed on screen.
This policy - implemented by the rules engine - resulted in eliminating nearly all of the needless "send officer" calls for this type of alarm. Additional rules were put in place so that if a high number of "door forced open" alarms occurred at around the same time, they would be reported because of the likelihood that a threat of some kind was causing an evacuation.
Increasing Security Effectiveness
Rules-based systems can bring situational awareness and security process effectiveness to levels that are simply not possible with manual processes or simple alarm automation. Now, the workflow management capabilities described can be applied within Security to significantly increase the effectiveness and efficiency of administration and operations without requiring an increase the number of personnel.
(PDF supports this article - download for large image format)
Ray Bernard, PSP, CHS-III is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities. Mr. Bernard has also provided pivotal strategic and technical advice in the security and building automation industries for more than 20 years. He is founder and publisher of "The Security Minute" 60-second newsletter (www.TheSecurityMinute.com). For more information about Ray Bernard and RBCS go to www.go-rbcs.com or call 949-831-6788
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.