In today’s interconnected universe, network and sensor outages in one system often have cascading impact on other systems with which they interact. For instance, a communications failure of one of the world’s largest airline carriers affected for not only the travel industry, but also the logistics and distribution of consumer goods. Very recently the failure of a sensor network shut down the largest petroleum refinery in the Midwest, causing the wholesale price for gasoline in Chicago and St. Louis to jump 60 cents per gallon in a single day.
A fault in a submarine optical fiber cable connecting Australia, Guam and Japan also recently failed; however, hundreds of gigabit per second data traffic from the impacted section was switched to alternate paths on an optical fiber ring configuration. If this resiliency had not existed, the outage could have potentially shutdown untold numbers of credit-card purchases, ATM money withdrawals and vital healthcare teleconferencing while awaiting a cable repair ship to reach the site and repair the damage.
And then, of course, there are the deliberate saboteurs. When internal technical issues simultaneously affected operations at two global financial exchanges, communications in the "Dark Web" congratulated the perpetrators on a job well done referencing the institutions by name. Chances are you're not very familiar with this shadowy network of websites often used to sell illegal goods and services. But ironically, the Dark Web itself was shut down recently when someone discovered services protocol vulnerabilities that could reveal the location of supposedly anonymous servers. Essentially, the hackers got hacked.
So what can we do as manufacturers, system architects and users to protect ourselves against such catastrophic events, whether initiated accidentally or maliciously?
Establishing trusted access authentication for IoT devices
According to a recent study conducted by Capgemini Consulting and Sogeti High Tech, the two most significant vulnerabilities in the world of IoT devices are password attacks and identity spoofing. This has led developers to devise better processes for establishing trusted access to the IoT, including server-based authentication.
One approach has been to base cybersecurity on server locations that are far away from the devices connected to the Internet – the "things" in IoT. However that method tends to slow down traffic. A faster alternative is to use multi-factor authentication (MFA) which permits multiple servers located closer to the "edge" IP cameras, physical access control panels and/or communications devices to process authorization requests.
Push Notification Services. One of the best examples of these high-performance security processes is the smartphone in your pocket or handbag. Push Notification Services (PNS), a highly efficient and secure remote notification feature for Android, iOS and Microsoft smartphone devices establishes an encrypted IP connection with the PNS and receives notifications over this connection. If a notification for an app arrives when that app is not running, the device alerts the user that the app has data waiting for it. When new data for an app arrives, the provider prepares and sends a notification to the PNS, which pushes the notification to the target device. This process also works with other IoT devices, sensors and even IP cameras.
The PNS establishes peer-to-peer authentication in the IoT sensor identity Transport Layer Security (TLS). The IoT device initiates a TLS connection with the PNS, which returns a digital certificate from the server. The device validates this certificate and then sends its device certificate to the PNS, which validates that certificate. PNS servers also have the necessary certificates, credential authority certificates, and cryptographic keys (both private and public) for validating connections and the identities of providers, corporate servers and IoT devices. This provides a more secure alternative to SSL, especially considering the latest PCI-DSS 3.1 compliance requirements
Whether it is a text message, video stream or complete digital multimedia content (video, audio and metadata), this process to establish trusted identities is the cornerstone of IoT device cybersecurity.
Alternative ways to harden against vulnerability
Looking back at the high-speed submarine cable incident, there’s obviously a need for resilient connectivity to maintain service and protect against attack. Although different transmission modes provide for connectivity, the architecture should also include authentication of the devices on the network. So why not just use "sat-backup" to keep authentication servers connected? The issue is response time agility. The total carrying capacity of a typical submarine cable between the U.S. and East Asia is in the range of terabits per second compared to satellites which typically offer only around 1000 megabits per second. The "Cyber Cloud" operators, governments and enterprises need the ability to quickly deliver differentiated services by activating, on notice, a virtual pool of bandwidth through resilient architecture.
Our petroleum example is another case in point. If caught in time, the IoT sensor network responsible for detecting leaking pipes would have notified plant operators in real time to implement a repair. Should a petroleum refinery flow sensor or server come under attack, the usage archives or historical data could be compromised. A cyber-attack on a refinery during peak winter (heating) or summer (automobile usage) periods could be catastrophic. Protecting IoT sensor data in motion is important, but intelligence in the wrong hands can be deadly. This is what cyber resilience is all about: not only protecting the operation and transmission of data, but preserving "data at rest."
The business case for investing in IoT safeguards
We know what we need to do to protect IoT devices. But how do corporations cost-justify investing in these safeguards? The answer is to expose risk management professionals to the daunting consequences of suffering a breach:
- class-action lawsuits
- regulatory fines, penalties and consumer redress
- damaged reputation
- data and income loss
With successful cyber-attacks on the rise, up from 11 percent in October 2013 to 16 percent in 2014, according to a recent survey analysis from Heavy Reading, many companies are reaching the point where the cost of deploying in-house authentication servers is well-worth the risk mitigation.
Damage from escalating cyber-attacks has also given rise to a new type of insurance category: cyber security insurance that covers both network security and privacy liability (see table pictured above).
But even with authentication servers and cybersecurity insurance in place, there’s another tough decision for a company to make: whether or not to share their threat intelligence. Does an enterprise keep their name out of the headlines as the yet another victim? Or do they contribute to a safer and secure world by pooling their ideas and strategies on how to combat cybersecurity attacks?
As a leading cyber security consultant recently stated, "When it comes to cyber intelligence, there's strength in numbers."
Creating multiple security layers for everyone
The Internet of Things in safety and security represents a networking paradigm where interconnected, smart sensors are powered and protected and continuously generate and transmit data over the internet.
Multiple layers of protection are needed to secure the operational integrity of those IoT sensors. Those layers include:
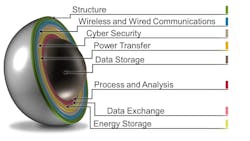
- IoT device structure – This can include the physical housing of an IP camera, as well as a wireless communication antenna and solar energy collection device.
- Wireless and Wired Communications – This refers to how the device connects to the local area network via Ethernet, Bluetooth or other connectivity as well connectivity to the internet.
- Cybersecurity – The heart of the external, internal cybersecurity and device protection functions, this layer also serves to assist in MFA.
- Power transfer – This is where energy for storage is acquired such as wireless charging or energy harvesting.
- Energy storage – Primarily this is where volatile data storage and processing functions occur.
- Data exchange – This layer performs protocol negotiation and ensures interoperability.
- Process and Analysis – This is where metadata analysis, energy management, storage optimization and indexing processes occur.
- Data storage – This is where the sensor data from all the "Things" in IoT are archived.
Striking a balance between protection and responsiveness
The trick is to devise those layers of protection without compromising the ease and timeliness of data interchange. Communication, storage, process, data exchange, security and device power are the defining factors in the IoT model structure.
Depending on the urgency of the response required for the event, there may be a need for the device to process certain data internally. In the case of an IP camera, for example, there is metadata that describes size, color, speed, trajectory and timeframe which may be needed urgently. For instance, the license plate of a vehicle associated with an amber alert, an armed robbery or other time-sensitive emergency.
IoT data may statically reside internally, immediately nearby or in mobile objects and IoT data concentration storage points. The data may be distributed widely, but it always must be transmitted and stored securely. The migration or "flow" of IoT data can continue from one secure container to another, until a centralized data store is reached where more sophisticated processing and analysis takes place, like facial recognition or other pattern matching algorithm.
Cyber protection is a joint responsibility
Consider the IoT sensor less of a "razor blade" and more of an evolving device and resource. Its most vital part is often its data, which forces us to make important choices about how we handle it: how it is collected, how it is stored, how it is processed and how it is protected.
With this foundation we can expand our use of IoT to a wide range of data types and formats from different data sources, including time and geo-location tags, and global intelligence. By pooling our knowledge about ways to protect these resources we can minimize our vulnerabilities to cyber-attacks even as they continue to evolve.
About the Author: Steve Surfaro is the Industry Liaison at Axis Communications. He is also Chairman of the Security Applied Sciences committee for ASIS International. He can be reached at [email protected].