Enterprise security risk management (ESRM) is a strategic approach to security management that ties an organization’s security practice to its overall strategy using globally established and accepted risk management principles. ASIS International began incorporating ESRM as a global strategy for security executives in 2017, and a resulting ESRM Guideline was published in 2019.
ESRM is a heady concept that requires study for security executives to become proficient; however, using ESRM can also be vitally important to security integrators who are working with these “prospects” – often a Chief Security Officer, security manager or their designated representative.
I often ask enterprise integrators how they are marketing their products and services. I ask if they are content with current sales levels, number of clients and profit; and how long the sales cycle is for a new client.
Most importantly, I ask them what problems they are solving for their customers. In the context of security, selling is about solving customer problems and creating value. Enterprise integrators should be working with a goal of genuinely creating value with their solutions. They should understand a customer’s issues or concerns as their marketplace evolves, their risk changes, and their needs change.
This is where ESRM comes into play, as it can provide the framework for integrators to focus their solutions on problem-solving and creating value; thus, creating a successful path to being a trusted advisor and an ongoing business relationship.
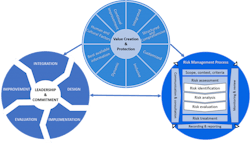
The ESRM Lifecycle
There are four steps to the ESRM lifecycle:
- Step One – Identify and prioritize assets: The process of identifying, understanding and prioritizing the enterprise’s resources, which can be people, intellectual property, manufacturing facilities, critical equipment, research, and more.
- Step Two – Identify and prioritize risks: Identify, understand and prioritize the risks to the enterprise and their relationships to the value of the assets. Risks can be human-made, for example, crime, terrorism and civil unrest; technological, such as an industrial accident; or natural, such as pandemics.
- Step Three – Mitigate the prioritized risks: Take necessary, appropriate and realistic steps to protect against the most severe threats and risks.
- Step Four – Continuous improvement: Managing risks requires a cyclical approach to continuously improving and advancing the enterprise’s risk posture.
In this context, integrators and consultants solve a client’s problems by aligning risk, threat, vulnerability, and consequence with mitigations, thereby eliminating or minimizing risk, consequences, and their impact on the Enterprise.
For every identified risk, there is a vulnerability, consequence, impact, and mitigation. Post-implementation, the client benefits from the value gained in reducing risk and ensuring the Enterprise’s strategy is successful.
Finding the Value in ESRM
To gain a better understanding of where the value resides, take a closer look at consequence and impact. Consequences are the terrible things that happen if a threat is successful, and the impact is the effect of consequence on the enterprise. Of course, there are many different consequences resulting from crime, terrorism, natural disasters and accidental hazards; however, most impacts fall into one of four primary buckets:
- People: Loss of life, injury, and loss of expertise.
- Finances: Impacts the enterprise’s financial health. If the economic impact is significant enough, the enterprise will cease to exist.
- Reputational: These impacts can have a significant financial effect, as customers may seek services elsewhere.
- Equipment: Impact to critical equipment and processes, the loss of which could be devastating to the enterprise.
The value of ESRM resides in understanding the cost of impact and the total cost of ownership. Case in point: A large warehouse loses $500K a year in shrinkage due to criminal activity. The integrator recommends mitigating the shrink with a $150K physical security system. If the system has an eight-year life, the enterprise will realize a net revenue increase of $3.85 million. In this case, the physical security system is a good investment that makes business sense. No selling is needed.
Thus, armed with the needed information to facilitate value-based decisions, integrators can make a complicated sale look like a “no-brainer.” Finding this information is obviously paramount, and to do it, integrators should refer back to the first two steps of the ESRM lifecycle (identifying and prioritizing assets and risk).
The Backbone: A Risk Assessment
Integrators and end-users can achieve the first two steps in the ESRM process through a comprehensive risk, threatThe ANSI/ASIS/RIM Risk Assessment Standard defines risk assessment as “the identification, analysis, and evaluation of uncertainties to objectives and outcomes. It provides a comparison between the desired/undesired outcomes and expected rewards/losses of organizational objectives. The risk assessment analyzes whether the uncertainty is within acceptable boundaries and within the organization’s capacity to manage risk.”
As an enterprise security integrator, you should not be developing solutions or making technology recommendations without understanding the client and their particular problems. Risk, Threat and Vulnerability Assessments are often misunderstood, and therefore misapplied. Risk assessment is not merely identifying risks and calculating a risk level; instead, it should be an entry point for identifying and quantifying all enterprise risks. Further, it is a process of continuous improvement which ensures the accomplishment of the enterprise strategy.
From an integrator’s perspective, you can train an in-house person or engage a reputable consultant to assist with a risk assessment. Once you know and understand the risks and their impacts on the enterprise, it facilitates exceptional decision-making from a business perspective as well as technology-based mitigations that address the client’s strategic risk.
ISO 31000 provides direction on how companies can integrate risk-based decision making into an organization’sThe actual value of a comprehensive risk assessment is found in the reduction or elimination of risk, which can impact the enterprise strategy, improvement in the quality and delivery of security services, enhanced security posture, and significant cost reduction by identifying inefficiencies.
A proper risk assessment accomplished by executive-level practicing professionals using the correct business-friendly tools will provide integrators with the analytical tools and business intelligence needed to identify the value in risk and make sound business decisions for their clients.
Tying the Results to the Client’s Business
Business intelligence is vital in identifying the value in risk assessment. Business intelligence facts create improvement in the bottom line and establishes the security function as a valued and trusted partner in the enterprise.
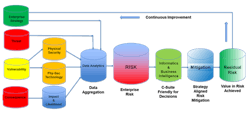
Integrators must manage, analyze, and interpret data to identify the best ways to address risk, demonstrate value, and support an enterprise strategy. Data analytics and informatics – which portray the collected data – are both essential for success in this regard. The resulting facts provide the information which clarifies and supports the business case.
Analytics and informatics data is displayed through user-defined reports, graphs, charts, etc., in meaningful ways to help demonstrate how the organization can improve its risk position, understand the value in risk, and make risk-based decisions. They provide a persistent risk picture, enabling the client’s leaders – often coming from a variety of departments and disciplines within an organization – to easily visualize improvement over time instead of a traditional one-and-done risk assessment. The improvement over time ensures a sticky process where the integrator supports a valued long-term client.
ESRM Pays Dividends
This detailed methodology for leading with risk as a business model for integrators has been proven by my company, Setracon ESRMS, many times over the past 11 years. Once we complete a risk assessment, we have identified upwards of $4.5 million in justified mitigations – each of which is tied to a risk, threat, vulnerability and consequence that can significantly impact the enterprise. The consequences and potential impacts are detailed.
The conversation that follows is not simply a security sales conversation – it has now evolved into a C-suite discussion where executives will decide to accept or mitigate the identified risks with as much data and information as possible from both a security and overall business operations standpoints.
There is value in risk, and integrators can significantly boost their enterprise security businesses by adopting an ESRM mindset and using ESRM as a practice.
Jeffrey A. Slotnick, CPP, PSP, is President of Setracon Enterprise Security Risk Management Services (www.setracon.com). Mr. Slotnick is an internationally known Senior Enterprise Security Risk Consultant with more than 28 years of experience.