Q. How do you determine if your customers are cloud ready?
Shayne P. Bates, CPP, CCSK, CHS-V, FABCHS, security strategist, advisor and advocate, Washington, D.C., who blogs at http://www.cyber-crime.biz: The cloud is a business proposition based on the things you need to do with technology to meet business requirements. Cloud services provide five core characteristics that are well defined by NIST. One of these is rapid elasticity. With Software-as-a-Service (SaaS) you are renting an app in the cloud, not buying it. In fact, with almost all cloud types the core idea is to rent services rather than own. Those services can range from infrastructure, to operating systems, to an application. When organizations invest in buying a traditional IT infrastructure, the design (and cost) is usually based upon peak-time load. This model is usually comparatively more expensive and becomes a relic of the past if you can access an available infrastructure that provides a pay-as-you-go charge model. With the perception of infinite compute, capacity is not an issue and organizations can rapidly expand or contract infrastructure based on requirements. If you don’t need peak load all the time, then why pay for it to sit idle?
Ed Meltzer, president, Security, Cloud & Mobile Partners LLC, Kansas City, Mo.: Being ready for the cloud requires a complete understanding of what it provides and what expected value propositions come with its adoption—in addition to shortcomings and risks. Cloud computing offerings in general are shared infrastructure, storage and network resources (IaaS) and applications (SaaS) typically provided by third parties via a Web browser and the Internet. Lower costs and variable cost structures, speed of application deployment and universal availability are key benefits that translate into promised lower costs. Risks associated with cloud computing include security, data portability and promised scalability under real-world production environments. Understanding both sides of the equation is the initial criteria to determine whether you are ready for cloud services, both as a provider and user.
Bill Moran, vice president of Sales, Red Cloud Security, Sterling, Va.: If you already sell Physical Access Control Systems (PACS), the good news is that the cloud is ready for you right now. Public- or private-cloud-based PACS solutions allow dealers and integrators to offer a Web-based security system as a hosted or managed service that is much easier to deploy, service and maintain than legacy, software-based security systems. In some cases, converting a legacy system to cloud-based PACS system only requires a new front-end system to manage the facilities’ existing door controllers, hardware, readers, switches, wiring and/or wireless locks and communication electronics.
Steve Surfaro, security industry liaison, Axis Communications, Chelmsford, Mass.: You have to understand what the customer needs and match that with the integrator’s business drivers. One driver is ease-of-provisioning network cameras for both permanent and temporary use. Today’s managed video technology can authenticate network video cameras instantly and securely in a single “one-click” step, eliminating lengthy manual parameter entry. If the client has numerous sites with low network device count and random footprint, a cloud service is a perfect complement and this simple provisioning service alone will build savings. A working knowledge of Service Level Agreements (SLAs) and tools to measure a service provider’s financial health are prerequisites for both parties.
Q. What are some criteria for being ready for cloud services?
Bates: There are four steps: first, if your cloud is offsite or public in nature, existing infrastructure and resources may be redundant, therefore it makes sense to divest yourself of unneeded technology and find a skilled partner. I call this “Divestment and Partnership.” Sometimes this partner can come from inside the organization, such as the IT department. Second, plan to virtualize existing systems to achieve “location independence” and have choices about where your apps and data will live. Technologies for this include Hyper V which comes with Windows 2008 Server, VMWare or similar. Third, for achieved location independence, decide where these core business functions should be hosted. Fourth, in the course of time, migrate from hosted apps to “native cloud” apps. If migrating existing apps, this is achieved by improving, re-developing and migrating code in future versions, so it is structured to take advantage of the five characteristics mentioned earlier. This is where the real cloud benefits occur; the first three are preparatory in nature and should only be seen as being similar to a traditional hosting scenario. Native Cloud is where the action is, but it cannot be achieved without thinking through how existing business processed will be improved and those served by apps will be migrated. This is why startup organizations today have such an advantage, they do not have legacy apps to be concerned with, nor do they need to purchase infrastructure and many functions and services have a transaction cost close to zero.
Meltzer: One of the primary advantages of public cloud offerings is that you do not have to make the infrastructure and personnel investments normally associated with private cloud deployments. Other factors in determining whether to go public or private, or even attempting a hybrid combination of the two include issues with your data leaving your facility and whether there are issues with your application being virtualized with many others.
Moran: Your systems and services offering is most important. If you want to manage and/or host PACS as a cloud solution and sell it as a service to your customers, then partner with a manufacturer that enables you to do so. You can also broker cloud services from a SaaS manufacturer, although in many cases they end up owning the customer. Many suppliers can help your organization prepare to deliver cloud services to your customers, so it’s important to evaluate which suppliers are the best fit for your preferred business model.
Surfaro: A user’s facility locations and the complexity of their security needs will determine their evolution to managed or hosted services. If a user plans to use mobile devices as an integral tool for surveillance and physical security management, they are best served through cloud platforms because they’ll have both varying platforms and connectivity. Video can be streamed across multiple mobile broadband networks to many different platforms and cloud users will receive consistent content from one authenticated source. The behavior of usage is also a criteria. Do you have predictable or random peaks in usage? Is your usage expanding, but you do not know the rate or scale? All of these benefit from the elasticity or ability of the cloud to closely follow usage with performance and service— delivering, not wasting, services to the user. Finally ask: Can the user benefit from verifiable data that is accessible by multiple users from a secure location?
Q. Are there customers not suited for cloud services?
Bates: While the cloud may not be appropriate for all situations, it is such a compelling proposition for most businesses because it makes so much sense from a business case perspective. It is a reasonable proposition for most enterprises to consider that every app is a candidate for the cloud, whether that cloud is on-premise, or off premise in a public cloud, or a combination of the two. Devices that lives depend upon, like fire alarms, will likely be the last into the cloud because of proven performance and code and regulatory concerns.
Meltzer: I don’t believe there customers or markets that are naturally excluded from cloud computing opportunities. The appropriateness lies more in the area of the application and the characteristics of the application or data therein. There are certainly applications for most companies that are suited for the cloud. However, heavily regulated and compliance-driven markets may have more challenges justifying cloud-based services. The Sarbanes-Oxley act, as an example, requires that organizations maintain email for seven years and have it available for audit in an expedient timeframe.
Moran: Typically there are no limitations; however in certain high-security sectors, such as nuclear facilities, that follow specific security system regulations from the NRC, cloud-based services may not be an approved system architecture as of yet.
Surfaro: With the array of service-provider offerings greatly expanding, this list is getting smaller and would include users with little or no Internet connectivity. While camera count typically determines viability for hosted video, users having highly complex requirements, large camera counts, access points or intrusion sensors can still benefit from “private” cloud deployments.
Q. Should you start your own cloud service?
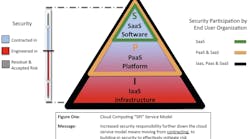
Bates: Decide what kind of cloud best matches the business and use case scenario, and which services you need: whether SaaS (Software-as-a-Service, PaaS (Platform-as-a-Service), or IaaS (Infrastructure-as-a-Service). There are four cloud types: private, community, public or hybrid. If you are a large enough organization, a private cloud for services to share only with your community of users might be best. It requires a good IT staff and expectations around what will be delivered and also the availability. A community cloud allows several agencies that share the same concerns to access information. Many security companies are looking at using public cloud infrastructure to host their security applications as they do not need to invest the millions of dollars involved in owning and maintaining infrastructure and platform. By selecting this PaaS option, these companies can effectively offer their own SaaS service. Another example of SaaS would be Microsoft’s Office 365 or TurboTax that you pay just for what you use.
Meltzer: Starting your own cloud service is technologically not a challenge. But like any business, there are costs to consider. Starting a cloud-based initiative brings with it a host of other considerations including security, reliability, resilience, data storage and infrastructure redundancy. There are legal considerations. By offering these services will there be
regulatory and compliance issues that you will be signing up for.
Moran: Whether you offer a public or private-cloud service depends on the IT infrastructure you prefer to manage, the sophistication of your competitors, as well as the needs of your existing customers and prospects in your market. For example, a small, local hospital may want the convenience of cloud-based access control but not want their security information hosted in a public cloud environment along with other customer data. In this case, you could configure a 100-percent, Web-based access control network appliance and host the system for the hospital as a private-cloud solution.
Surfaro: With a larger choice of managed or virtualized physical security offerings out there today, there is a greater demand for the “cloud broker” or service reseller (SR) to qualify and match their services with SLAs to appropriately capable service providers (SP). The SR’s return on investment (ROI) is far faster than that of an SP, as there are far less depreciating investments and a greater reliance on skilled professionals to act as cloud consultants or service agents. An SR may move into a hybrid SR/SP role by accumulating monthly revenue shared with another SP. The SR may realize that the diversity of markets requiring cloud services is so great that the manpower must be allocated to seeking out potential users rather than delivering the actual services. SPs may add reseller roles internally but, to scale as fast as possible, the establishment of a cloud services reseller partner program is both essential and rewarding. With logical and cyber security improving, the decision to use a public or private cloud is getting more difficult.
Q. What’s involved in servicing customers using the clouds?
Bates: As a security practitioner you have to have controls in place to mitigate risk with compliance, privacy, security and other factors associated with risk management. If you take a SaaS application, someone else has complete control of everything; your data, the application and your computing infrastructure. Build trust. Have sufficient contract provisions to protect data and validate those controls are real using an independent source.
Meltzer: Servicing includes both sales and support. For cloud-based video applications you will need staff and personnel that are completely familiar with networks and bandwidth utilization and IP camera technology. And then you will also need personnel well versed in video itself. At a minimum, IT-trained personnel are a must as are specialists in the cloud-based applications you offer. There are new considerations in the areas of service and maintenance. The traditional SLA specifies performance and response, but only after quality of service (QoS) has been defined and real-time monitoring and enforcement have been negotiated. You need to ready yourself for the adoption of SLA-based services, versus the traditional liability limiting indemnifications such as those found in alarm monitoring agreements.
Moran: You could provide on-site response and system administration as a bundled service offering, establish pricing and implement a recurring monthly revenue model. Some manufacturers already offer their access control systems to dealers on a monthly subscription basis, allowing them to resell the systems to customers on a pay-as-you-go model without purchasing the entire system up front, making the transition to a cloud-service offering even easier.
Surfaro: Since there is no software to go out-of-date and create potential compatibility issues, cloud SPs focus on endpoint device firmware, usage, and connectivity checks along with network health, power and virtually limitless report configurations. Data “dashboarding” is popular. The SP can provide the data the user needs, when they need it and on any platform.