This article originally appeared in the June 2021 issue of Security Business magazine. When sharing, don’t forget to mention Security Business magazine on LinkedIn and @SecBusinessMag on Twitter.
Perimeter security solutions for aviation, critical infrastructure, logistics vertical markets and high-value soft targets are increasing in priority and value.
To illustrate, back in September 2020, the Trump Administration authorized more than $1.2 billion in grants for airport safety and infrastructure through the Federal Aviation Administration (FAA)'s Airport Improvement Program (AIP).
Scanning though GAO and FAA documents, many of these grants go specifically to address perimeter security and access control. Examples include $30 million to install a full biometric access system; $6.5 million to install over 8,000-foot-long blast/crash resistant wall along the airport perimeter; $8 million to install over 680 bollards in front of passenger terminals and vehicle access points; and $3 million to develop and install an infrared intrusion detection system.
Securing a perimeter in virtually all facilities with a 24-hour flow of public safety individuals, employees, visitors and vehicles incorporates credential and identity verification, vehicular and shipment inspection, and monitoring for firearms and contraband.
Manned and unmanned vehicular entrances can be enhanced with fast and accurate automatic number plate identification (ANPR) that not only archives vehicle make, model and speed, but will also keep real-time status if the vehicle is overdue for exiting out of the campus. Also, AI-based vehicle undercarriage inspection systems are becoming a necessity in public venues. These systems compare current views with archived imaging and those provided in a vehicle manufacturer’s database.
3D Space Protection through Object Recognition
Incorporating a full perimeter security strategy poses significant costs, and most corporate facilities can have risk reduction by leveraging newer technologies at lower costs, thanks to advancements from other industries.
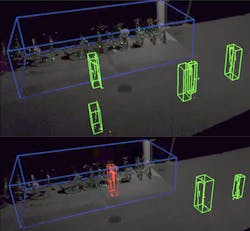
The autonomous vehicle industry has made the use of stationary versions of LiDAR (light detection and ranging) affordable for space protection. The LiDAR point cloud generated for autonomous vehicles is like a 360-degree photo that is captured over a period of 100 milliseconds and allows cars, bicycles, and pedestrians to be categorized and recognized.
LiDAR solutions for the security and safety industries also detect vehicles and humans and their direction, with additional threats like potential explosive objects and their proximity to facility power plants, telecommunications, and high-value product storage.
Leica Geosystems recently introduced a “3D reality capture sensor for surveillance” that differentiatesbetween still and moving objects, detects various changes in both sunlight and darkness, and frame critical areas with digital fences while guaranteeing total privacy. Typically deployed in public spaces like transportation, smart buildings, hospitals, schools and museums, the capture sensor uses AI, 3D digital fencing, edge computing and LiDAR-enabled change detection technology to identify security threats and provide real-time alerts for both expected and unexpected changes.
Although products like this are detecting in three dimensions, and their renderings are displayed on two dimensional monitors. The ability to re-orient the special view will be relatively simple for command center applications not restricted to video management.
With the threats of rogue drone operation, potential of nearby rioters throwing incendiary devices, or perimeter incursions from points undetectable by ground level sensors, three-dimensional visualization literally adds new perspectives on reducing facility risk.
Adding the “time” component to a perimeter visualization will reveal subtle changes over time to the perimeter. They could be natural – the need to clean up brush and flammable debris; or manmade, like vandalism to barriers fences that go undetected until a breach occurs.
Drones add a new dimension to perimeter security, whether the end-user deploys a cUAS solution monitoring the airspace above and around a facility or leverage the use of “mission” drone launches that enhance other space sensors like LiDAR or visible light/thermal imaging dual sensor cameras.
One such solution is an Unmanned Aerial System – Security Deployment System (UASSDS) that, on sensor(s) activation, launches a UAS from an enclosure, surveys a facility, transmits encrypted comms and video, allows stationary or mobile staff to take active flight control or just monitor a preprogrammed series of waypoints in three dimensions, return to launch pod/enclosure and commence a recharge cycle. The self-deploying drone system, provided by Oculus Deus LLC, can leverage visible and thermal imaging, direct the drone to waypoints indicated by stationary LiDAR sensors or other cameras and deliver a tactical response.
Weapons Detection
Firearm discharge and detection of active assailants are becoming critical parts of a facility’s perimeter – both outdoors and in interior spaces. Wireless sensors like the Firefly and CityWeb by EAGL process acoustic events based on energy level analysis – if a firearm discharge or gunshot is recognized, ballistic identification and location is provided to the monitoring system.
Video surveillance systems can be enhanced with AI-based weapons detection system even before afirearm discharge occurs, such as with the Concealed or Visible Gun Detection System by Athena Security. Both elevated temperature for health screening and concealed gun detection are accomplished at perimeter public and employee entrances using front and rear facing multi-spectral sensors.
Reliable firearms detection is a valuable opportunity for a public/private partnership, in which local law enforcement and businesses collaborate to prevent the loss of life, and security integrators are obviously vital in deploying this type of technology.
Protecting the Cyber Perimeter
Perimeter security and safety solutions protect, but they also leverage IT Infrastructure. What solutions are on the network? Identifying all hardware and software present on the network requires the tracking and management of software and device firmware revisions. Managing who is on an IT network requires the control of user accounts through identity and access management.
Like perimeter security, network security management is intended to provide extensive and dynamic monitoring of the security controls, leveraging AI and protecting against attacks involving multiple vectors, behavior and distribution of rogue actors.
The Environmental Perimeter
An often-overlooked aspect of perimeter security is environmental and air quality management. AerNos Inc., of San Diego, was the a winner of a CES Innovation Award in 2020 for nano sensors todetect harmful gases like methane and carcinogens like the sweet smelling but lethal benzene. The sensors can exist in stationary form factors for smart city environmental safety and on drones for critical mobile sensing at or near utilities and refineries. These sensors can also provide for early warning of wildfires in many use cases, as well as safety monitoring of firefighter first responders.
For indoor detection, AerNos earned a 2021 CES Innovation Award for its AerHome sensor system, which brings valuable hydrocarbon and air quality measurement to homes and SMBs, processing data from environmental nano gas sensors through an artificial intelligence (AI) software app and delivering an air quality diagnosis.
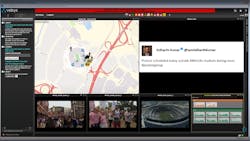
Putting it all together: Unified Situation Awareness
Trace a physical or virtual protection path around the circumference of a soft target, surround it with sensors and you have taken a first, important step towards physical perimeter defense. The next step is to create a virtual perimeter, which can be “drawn” to search for public posts and social media language that could reveal potential threats. A Social Media Accumulator application, for example, reports the use of violent keywords, names of soft targets or gang-related language. The final step is to bring it all together. Unifying sensor detection and related situational awareness updates, as well as historical situational awareness data is now a requirement for single-platform users.
The basic framework that built yesterday’s physical security can be applied to today’s unified safety/security designs:
- Deter: Physical security controls that deter an intruder are intended to reduce the intruder’s perception that an attack will be successful, like an armed officer.
- Detect: The use of reliable and advanced technology supported by a Security and Safety Plan.
- Delay: The fusion of physical and virtual barriers, such as perimeter fences and space detection with object recognition.
- Deny: Manned and unmanned vehicular and personnel entrances enhanced with ANPR, health screening and firearms detection, and gunshot/discharge detection.
In addition, the need for perimeter security can be quantified using the following formula: Risk = Threat x Vulnerability x Consequence. A threat is a natural or man-made occurrence, individual, entity, or action including lethal physical, environmental, biological or cyberterrorist attacks; vulnerability includes human, physical, IT or infrastructure assets are open to exploitation and damage; and consequence includes the effects of an event attack or occurrence – either through terrorism, cybercrime, weather, biological or hazardous threat – resulting in life safety, public health, and economic loss.
One example of s system to unify all of this information would be Vidsys, a platform that started as aSteve Surfaro is Chairman of the Public Safety Working Group for the Security Industry Association (SIA) and has more than 30 years of security industry experience. He is a subject matter expert in smart cities and buildings, cybersecurity, forensic video, data science, command center design and first responder technologies. Follow him on Twitter, @stevesurf.