I can’t imagine that any security practitioner who has had even the most cursory contact with the news in the past decade could be unconscious regarding the insider threat. Frankly, and depending only somewhat upon what business you are in, I can’t imagine any security manager failing to consider their company’s exposure to the knowledgeable insider adversary. They have the keys after all. Our national and financial security have been notably impacted by insiders exploiting defective internal controls and the respected Ponemon Institute annually publishes a litany of insider risk trends that underscore the cost of reputational risk by strategically-placed insiders in “positions of trust.”
Insider protection doctrine establishes several principles that drive the consideration of alternative approaches to performance measurement: 1) identify process criticalities and assess risk; 2) establish processes to assure trust in employee integrity; 3) foster deterrence through a security-aware workforce; 4) limit access to sensitive information; 5) employ responsive measures to monitor the effectiveness of information access and insider behavior; 6) detect anomalous or malicious activity; and 7) respond with timely and measurably effective remedies to such activities.
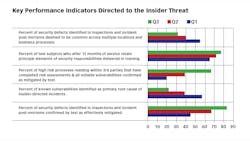
In spite of some published assessments that there are few if any metrics directed to measuring this sector of operational risk, I believe there are several areas of fruitful exploration for both risk and performance measures. The chart below displays just a few I feel are worthy of consideration.
Outputs of inspections, investigations and risk assessments — Assuming you competently inspect and assess to uncover defective internal controls or security measures and conduct internal investigations, these results should offer up a host of conclusions you have passed on to the business unit or process owner. What was the result of the steps they took to address these gaps and how measurably effective have those actions been to remove the vulnerabilities? Scoping process controls across the spectrum of delivery — this entails end-to-end analysis and addresses third-party ownership and effectiveness of insider risk management.
- Identifying and linking common denominators: Common defects in multiple locations and business units indicate more fundamental process defects that are likely indicative of more expansive vulnerabilities in process safeguards. Addressing these multiple threat vectors enable a more comprehensive and cost-effective mitigation strategy.
- Root cause analysis will identify and scope the defective controls to enable a more actionable and successful set of steps to improve deterrence, detection and response.
- Focusing the inspection and assessment processes on the lessons from incident post-mortems.
- Testing the effectiveness of the measures taken by process owners to address gaps identified in the risk assessments and then feeding back the results as required for assurance.
Employee engagement and security awareness — At the end of the day, insider protection relies heavily on a fully engaged and knowledgeable workforce. Assurance involves test and other methods of verification regarding the retention and quality of actionable knowledge of security responsibilities by persons in positions of trust. “Trust” is a core element in insider protection but experience has demonstrated that the combination of desire and exploitable opportunity can result in avoidable risk at various levels of severity. Maintaining in-depth safeguards and monitoring for anomalous and malicious or just plain risky behavior is an equally core set of activities to accompany trust in those with access.
George Campbell is emeritus faculty of the Security Executive Council (SEC) and former CSO of Fidelity Investments. His book, Measures and Metrics in Corporate Security, may be purchased at www.securityexecutivecouncil.com.