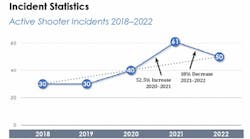
It is impossible to ignore the issue of active shooters in U.S. businesses today. The FBI recently released a report that shows these incidents steadily trending upward since 2018. The FBI only tracks those incidents that meet their definition of “one or more individuals actively engaged in killing or attempting to kill people in a populated area.” There are many more shooting incidents where weapons are involved which do not meet their definition.
One caution here is that some organizations place all their emphasis on active shooter training rather than taking a measured approach to the entire spectrum of workplace violence prevention with most organizations deferring to the original “Run, Hide, Fight” model of training. There are other models out there which can be considered such as
- ALICE (Alert, Lockdown, Inform, Counter, Evacuate), focuses on empowering individuals to make informed decisions based on their specific circumstances. It encourages people to be alert, gather information, and take appropriate action, including lockdown, countermeasures (if necessary and as a last resort), and evacuation.
- Avoid, Deny, Defend, which emphasizes three key actions. First, individuals should try to avoid the threat by escaping or removing themselves from the danger zone. If that is not possible, they should deny access to their location by barricading or securing the area. As a last resort, individuals may need to defend themselves against the attacker using whatever means are available.
To be totally effective against the active shooter, risk organizations need to address lower-consequence workplace violence events from the prevention versus the response side of an incident after shots are fired. Extremely violent events like active shooters originating from current or former employees, persons related to intimate partner or domestic violence and even clients and customers in some cases can be predicted and therefore prevented.
With a broader focus on workplace violence and educating employees on the importance of recognition, reporting and early intervention (e.g., with employee assistance programs (EAP) for employees for instance), the risk of an active shooter incident can be reduced. This article will offer other ways to reduce the active shooter risk by focusing on two types of violent offenders:
- The premeditated attacker; and
- A “heat of the moment” attack by some unanticipated provocation of the attacker.
There are two types of violence that should be noted in any discussion on workplace violence and active shooters which allow specific mitigation strategy considerations in reducing risk:
1. Targeted Violence. Targeted violence refers to acts of violence that are specifically planned and directed toward a particular individual, group, or location. Unlike affective violence, targeted violence involves a deliberate selection of the target and premeditation. It often involves detailed planning, surveillance, and a specific intent to harm or cause damage. The motivations behind targeted violence can vary widely, including revenge, ideological extremism, terrorism, or personal vendettas. Examples of targeted violence can include assassinations, mass shootings, acts of terrorism or hate crimes.
2. Affective Violence. Affective violence refers to a type of aggression or violent behavior that is driven by intense emotions or affective states. It is characterized by acts of violence committed in response to heightened emotional arousal, such as anger, frustration, jealousy, or rage. Affective violence often occurs in the heat of the moment, without careful planning or premeditation. It is typically impulsive and reactive, resulting from a loss of emotional control. Examples of affective violence can include fights between individuals, domestic disputes or assaults prompted by an immediate provocation. A weapons screening program which will be discussed later in the article can be a sound strategy when this type of risk exists.Considerations for Targeted Violence
Threat assessment and early intervention: A key element of workplace violence and active shooter program is a system for identifying and assessing individuals who may pose a risk of violence so the organization can intervene appropriately to assess, address concerns and provide the necessary support to redirect the person of concern. In almost every instance, inappropriate behaviors and/or communications by a person of concern preceded the violent incident. These are often referred to as “red flags” or “leakage.”
Red flags can manifest in various ways, including:
- verbal threats,
- aggressive or hostile behavior,
- expressions of anger or resentment,
- an obsession with violence or firearms,
- frequent discussions or references to previous violent incidents,
- or an intense fascination with mass shootings or acts of terrorism.
It can also include the individual expressing a desire for revenge or displaying a sudden change in behavior, becoming increasingly withdrawn, isolated, or prone to outbursts. These are examples of signs or indicators that an individual may display prior to engaging in violent behavior or acts of aggression in the workplace. The ASIS Workplace Violence and Active Assailant Prevention, Intervention and Response Guideline (WVPI 2020) recommend a multidisciplinary team trained to evaluate and respond to reports of “concerning behavior”. A threat management team would typically include human resources, security, and legal personnel.
Training and education: The red flags and leakage discussed above are signs, often observable through a person of concern’s behavior, actions, or communications, and may suggest a potential for harm or violence towards others but are only of any value when recognized and reported by employees and then acted upon by an organization’s threat management team. Organizations need to be conducting regular and recurring training sessions for employees, students, and staff members to educate them on recognizing potential threats and reporting suspicious behavior, so the organization can implement the appropriate response measures. Training must include communication of policies and procedures for handling security threats, including mandatory reporting, a multitude of reporting mechanisms, evacuation plans, and emergency response protocols.
Adequate security measures: Adequate security measures are determined by conducting a physical security risk assessment. At a minimum, security protocols must include controlled access points and proper vetting of persons prior to admitting them into the workplace. Other optional measures such as video surveillance systems, fencing and alarm systems, may deter potential attackers and enable quick response in case of an attempted breach of security.
For sites that may have an elevated risk of active shooter, hardening strategies are:
Collaboration with law enforcement: We encourage all our clients to foster strong partnerships with local law enforcement agencies to facilitate information sharing, joint training exercises, and coordination in response to potential threats. This has become infinitely more difficult with police agency staffing shortages, but attempts still need to be made. Typically, the discussions with local law enforcement would involve three areas of focus:
1. Crime trends and the potential and likelihood that consideration of an outside criminal as a source of workplace violence or active shooter should be included in a facility’s risk profile.
2. The services that a law enforcement agency may offer an organization to support a workplace violence prevention program such as termination standby or contracting for off-duty police to assist in protecting a site when there is an ongoing threat like an employee making a threat when being terminated; and
3. How the agency would respond to and enter all areas of a facility in the event of an active shooter. In the Virginia Beach shooting police were denied access to the shooter due to a card reader-controlled door. From the Virginia Beach Police Department’s May 31, 2019, Final Investigation Summary Report, “The officers were unable to pursue the suspect as they did not possess the necessary key card to gain access through the secured doors in the area.”
Creating a culture of civility and respect: It is important to promote a positive and respectful environment that encourages open communication, and respect for others and supports individuals who may be experiencing social isolation or bullying. There needs to be a strong position against workplace violence and the predecessors to violence some refer to as a zero-tolerance policy. Zero-tolerance does not work in all environments such as healthcare even though many hospitals tout a zero-tolerance policy. Federal law (Emergency Medical Treatment and Active Labor Act or EMTALA) prohibits hospitals from truly implementing this zero-tolerance policy.
The main purpose of EMTALA is to prevent hospitals from refusing emergency treatment or transferring patients based on their ability to pay. Under EMTALA, when a person comes to an emergency department seeking medical assistance, the hospital is required to provide a medical screening examination to determine if the individual has an emergency medical condition. If an emergency condition is found, the hospital must provide appropriate treatment to stabilize the patient, regardless of their ability to pay, insurance status or whether they have been involved in a previous act of violence.
Regular emergency drills and rehearsals: Conduct periodic active shooter drills to familiarize individuals and increase awareness of response procedures, including lockdowns, evacuations, and communication protocols, improving overall preparedness. One critical element of active shooter training is to encourage people to elevate their self-awareness. For instance, this type of training can enhance familiarity with surroundings. By participating in drills, individuals become more familiar with the layout of their work environment, including exits, lockable areas, and potential hiding spots, enabling them to make informed decisions during an incident. Individuals involved in active shooter incidents have been known to experience what is called normalcy bias.
When this occurs, they may fail to recognize the danger and delay taking appropriate actions to protect themselves and others. They might rationalize the situation, assuming that the sounds of gunshots are something else or that someone else will manage the problem. This bias can hinder their ability to quickly assess the situation and respond effectively, potentially putting themselves and others at greater risk. Training, drills, and education about active shooter situations can help individuals overcome normalcy bias by providing them with the knowledge and skills necessary to react swiftly and appropriately. By acknowledging the possibility of such events and mentally preparing for them, individuals can increase their chances of survival and aid in the protection of others during an active shooting situation.Considerations for Affective Violence
Weapons Screening: Weapons screening can be an excellent mitigation strategy when the risk profile indicates the potential for an incident associated with affective violence. People may possess a weapon but have no prior intention of using it when entering a facility, but some triggering event flares up the emotions and if a weapon is available, it may be used. By preventing the firearm from entering a facility an incident can be averted. The major cost of weapons screening is associated with the personnel operating it. Innovative technology can be acquired for $20,000 or less per lane of screening. There are several important considerations when implementing weapons screening:
· Risk analysis – prior to implementation, there should be a comprehensive analysis of potential threats and risks, particularly associated with affective violence. Places like behavioral health settings or government facilities (e.g., social services) routinely have these types of outbursts.
- Throughput needed – what is the volume of people that need to enter the facility at peak times? This will influence technology selection.
- Divesting property – this will also have a substantial impact on technology selection. We only know of two solutions in the marketplace that will allow for persons to be screened without divesting all personal belongings such as cell phones which do not pose a threat to an active shooter incident.
- Bag and package searches - as good as technology can be, the weak point is always the human element. In instances where a threat is detected for non-divestment screening or when bags must be manually screened where conventional metal detectors are used, the weak point is going to be sloppy protocols that may allow a weapon to enter the secure area even after bags and packages are checked by security personnel. This suggests a preference for the use of technology that does not require divestment or bag searches and a protocol that has the owner of the bag removing the item which has triggered the alert for visual inspection.
De-escalation and Conflict Resolution Training: De-escalation and conflict resolution training is a valuable tool in preventing active shooter events by providing individuals with the skills and techniques to defuse potentially violent situations before they escalate and can provide the ability to recognize the warning signs and indicators of potential violence. By employing effective communication and conflict resolution skills, individuals can help de-escalate conflicts and prevent them from turning violent. When compared with other facility hardening mitigation strategies such as ballistic resistant building materials or armed security personnel, de-escalation training is typically going to be a cost-effective strategy for reducing the risk of active shooter events.
Final Thoughts
Active shooter incidents are on the rise. Organizations need to assess their risk levels and determine the need for physical enhancements and training dependent on the specific risks faced. Mitigation strategies are dependent on whether the attacker is acting on premeditation or in the heat of the moment. There are several education and training options available that can help organizations to cost-effectively reduce the risk without a substantial capital investment for a low-likelihood event.
About the author: Frank Pisciotta, CSC, is president of Business Protection Specialists, Inc., (https://www.securingpeople.com/physical-security-system-design/) a nationwide independent security consulting firm focused on risk identification, regulatory compliance and security design services. Pisciotta has managed more than 5,000 security-consulting engagements in his 33-year consulting career. He is an architect of global security programs, possesses a master’s degree in public administration, a bachelor’s degree in criminal justice, and was board certified in Security Management by the American Society for Industrial Security as a Certified Protection Professional in 1994. He is also a Certified Security Consultant by the International Association of Professional Security Consultants. He can be reached at [email protected].