Understanding Customer Value
Both customers and service providers must grasp the difference between a technology “deployment” and an “installation” to avoid shortcomings in security system usability, reliability, and operational capability.
Q: At a few facilities, our security system installations and upgrades are supposed to be completed but problems continue to surface. Is this common?
A: This situation is not confined to the physical security industry; it is less common in the IT and manufacturing domains nowadays for many reasons.
Success in Other Domains
Success in most commercial domains stems from a strong focus on customer needs and requirements, which is essential for customer satisfaction. In the IT world, the first principle of the Manifesto for Agile Software Development centers on customer satisfaction. Also, in the IT world, the first step in Top-Down Network Design is focusing on customer requirements and business needs. My free eBook, Future-Ready Network Design for Physical Security Systems, explores what Top-Down Design means for networks, among other topics relating to customer value for networked physical security system designs.
In Lean Manufacturing, where Lean Principles are applied, the first Lean principle is to define what “value to the customer” means. Ryan E.B. Heri, a project management professional at Cognizant, explains this in his article, Five Principles of Lean Management. He has written a very insightful explanation of what customer value means and the lengths one may have to go to achieve it. Heri notes, “To better understand the first principle of defining customer value, it is important to understand what value is. Value is what the customer is willing to pay for. It is paramount to discover the actual or latent needs of the customer. Sometimes customers may not know what they want or cannot articulate it. This is especially common when it comes to novel products or technologies.”
Lean, Six Sigma, and Agile Development practices incorporate processes and steps to help customers define their technical and operational needs and expectations at the start and throughout the project. References to other customers’ deployments can be extremely helpful, especially with site visits that delve into how customers achieve and value significant benefits.
End-user customers, especially those most familiar with pre-AI-enabled security technologies, may lack insight into emerging breakthrough technologies. The value of these technologies, in terms of situation and incident detection, situation evaluation, intelligent notifications and workflow automation, is best understood in specific risk contexts and their preventive, preemptive, and impact-reducing capabilities. Modern technologies can be substantial force multipliers regarding the speed, effectiveness, and scalability of situation response handling, especially for multiple simultaneous incidents.
Determining Customer Value
Companies go to great lengths to determine customer value when designing software products and physical goods. In consumer products, for example, these efforts are a small part of each product's cost but pay off significantly through high sales volumes.
For small businesses with minimal physical security needs, determining customer value is straightforward and can be met by selecting from a wide variety of various vendors' products. Both traditional methods like trade show shopping and modern online shopping suffice for these systems.
However, this is not true for medium and large-scale enterprises with diverse physical security needs. Even companies in the same sector with similar numbers and types of facilities and employee counts may have vastly different security requirements due to specific risks to their facilities and critical assets. Thus, each customer facility requires a specifically designed security system deployment. While the various facility deployments can utilize the same types of technologies, how they are utilized and configured will have many site-specific elements.
No-Compromise Security System Deployments
What makes achieving high-customer-value deployments much more feasible than in prior decades is the fact that we have reached a watershed moment in the physical security industry: technology has advanced so much in capabilities and affordability that neither cost nor capabilities limit the operational value of security system deployments anymore. However, shortcomings in our approach to these deployments can.
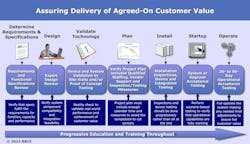
In the security industry, the terms “installation” and “deployment” are often used interchangeably, but they should not be. Installation is only part of the deployment process, which—if done correctly—includes many steps to ensure the work delivers the customer's desired value, including needs the customer may not recognize as crucial.
This is where sound system commissioning is essential. Commissioning goes beyond just “finishing the installation.” It ensures that systems are designed, installed, tested, operated, and maintained according to the end-user's operational requirements. It validates that all system components and subsystems function interactively according to the design intent and the owner's operational needs.
Today, the overall quality of technology in the physical security industry is substantially higher than in the past. Therefore, deployment issues often arise from process shortcomings rather than technological deficiencies. Effective customer education and training throughout the deployment, rather than just at the end, can accelerate project completion and reduce callbacks. Being thorough early in the project and avoiding shortcuts typically leads to shorter or non-existent punch lists, faster project completions, and less troublesome deployments.
A sound deployment process results in a customer being confidently ready to use the system and fully satisfied with the value received.
Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), which provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s Top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon.
© 2024 RBCS
About the Author

Ray Bernard, PSP, CHS-III
Ray Bernard, PSP, CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Ray has recently released an insightful downloadable eBook titled, Future-Ready Network Design for Physical Security Systems, available in English and Spanish.
Follow him on LinkedIn: www.linkedin.com/in/raybernard.
Follow him on Twitter: @RayBernardRBCS.