Two cybersecurity compliance and conformance programs - Underwriters Laboratory (UL) 2090 Cybersecurity Assurance Program and the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) lead the industry in providing guidelines and technical baselines that reduce the risk of cybersecurity breaches and attacks. Which one is more suitable for your needs?
As technology and network connected devices reach 20.4 billion devices by 2020 with predictions of cyber breaches costing six trillion dollars in 2021, how do we protect ourselves against self-imposed cyber-Armageddon? The one size fits all approach does not work with cybersecurity. One must be able to accurately assess and evaluate the risk level of the deployment environment where the product will be used.
The Answer Lies in Product Testing and Evaluation.
Over time we have seen proof that self-evaluation, self-governance, and self-certification have led to foundational cybersecurity failures – the industry has concluded that very few manufacturers are equipped and staffed appropriately to implement cybersecurity programs, not to mention technical countermeasures that uniformly protect their product lines against cyber threats. So how do we protect our agencies and organizations against ourselves? The answer is third-party assessments.
Now that the industry has recognized that formalized assessment procedures are both necessary and required, through U.S. Executive Orders and Presidential Directives, critical infrastructure protection sectors are finally confronted with mandated regulatory requirements to adopt cybersecurity standards and rigorous testing methods and processes.
These regulated and testing models and processes have become standardized to assert that security policies and practices are put in place to protect network-connected products, solutions, and devices that are delivered to the market. Both UL and NIST have very broad and distinct offerings, - we will detail each of them.
UL Standards
First, let’s examine the UL 2090 Cybersecurity Assurance Program (CAP). In the product manufacturing arena, UL gained its industry recognition for developing standards for life safety products worldwide. It makes great sense with the long reputation of UL that they offer a cybersecurity assurance program. The UL program provides very strong assurances that supply chain processes are validated and defined as part of its intake workshop. The CAP framework guides the manufacturer or vendor through a variety of phases that move into a product evaluation phase that tests the products against a variety of known security vulnerabilities and susceptibilities.
One of the very important benefits of the CAP program is that it is an American National Standards Institute (ANSI) certified program which is recognized throughout the world.
NIST Standards
Next, let’s take a look at the NIST Cybersecurity assessment standards. It has a core framework CSF, and an expanded set of controls that are tailored to achieve specific cybersecurity outcomes and references examples of guidance to achieve those outcomes.
The larger set of controls, the NIST Security and Privacy Controls for Information Systems and Organizations, encompasses a comprehensive assessment methodology that can apply to specific types of organizations, manufacturers, industrial control systems, defense and US Federal contractor protection of confidential and unclassified information, etc.
Which One Do You Choose?
Having performed security assessments using both UL and NIST cybersecurity standards and methodologies, I have concluded that both have their purpose, however, after personally performing the NIST Cybersecurity Framework and its expanded testing procedures I have found that they are much more complete in determining the security baselines an organization should choose to address relevant cybersecurity requirements.
The basis for my conclusion is that the NIST CSF is further broken down into categories comprised of four elements: functions, categories, subcategories, and informative references that are better for security professionals to follow during the assessment and evaluation of products and technologies. A description of each is listed below:
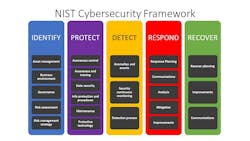
- Functions: There are five functions used to organize cybersecurity efforts at the most basic level: identity, protect, detect, respond, and recover. Together these five functions form a top-level approach in securing systems and responding to threats. Think of them as your basic incident management tasks.
- Categories: Each function contains categories used to identify specific tasks or challenges within it. For example, the protect function could include access control, regular software updates, and anti-malware programs.
- Subcategories: These are further divisions of categories with specific objectives. The regular software updates category could be divided into tasks like making sure wake on LAN is active, that Windows updates are configured properly and manually updating machines that are missed.
- Informative References: Documentation, steps for execution, standards, and other guidelines would fall into this category. A prime example in the manual Windows update category would be a document outlining steps to manually update Windows PCs.
Another reason I have concluded that the NIST cybersecurity assessment model is more relevant to manufacturers and the system integrator community is that the NIST Cyber Security Framework is a more descriptive way as to how the level of implementation can be evaluated more than a simple (yes/no) answer.
NIST Cybersecurity Framework Implementation Tiers
Using the NIST CSF, there are four tiers of implementation, and while CSF documents don't consider them maturity levels, the higher tiers are considered a more complete implementation of CSF standards.
- Tier 1: Called partial implementation, organizations at Tier 1 have an ad-hoc and reactive cybersecurity posture. They have little awareness of organizational risk and any plans implemented are often done inconsistently.
- Tier 2: Risk-informed organizations may be approving cybersecurity measures, but implementation is still piecemeal. They are aware of risks, have plans, and have the proper resources to protect themselves but haven't quite gotten to a proactive position.
- Tier 3: The third tier is called repeatable, meaning that an organization has implemented CSF standards company-wide and are able to repeatedly respond to a crisis. Policy is consistently applied, and employees are informed of risks.
- Tier 4: Called adaptive, this tier indicates total adoption of the CSF. Adaptive organizations aren't just prepared to respond to threats, they proactively detect threats and predict issues based on current trends and their IT architecture.
In-House versus Third-Party Assessors
Under the UL program, third-party subcontractors comply under its third-party test data program to support field activities and product testing on its behalf. These third-party testers conform to International Organization of Standardization, or (ISO). Most of the security benchmarking and testing under ISO is concentrated on the use of an Information Security Management System (cybersecurity objectives) primarily used by large organizations as a comprehensive organization risk management plan.
You will find ISO 27002 extensively used by multinational corporations and companies that do not have to specifically comply with U.S, federal regulations. ISO standards have been referred to as being “less paranoid” than NIST, which has an advantage of being less complex and therefore easier to implement. One unfortunate thing is that ISO charges for its publications, and charges for certifications under its UL Assessment program.
On the other hand, NIST Compliance is not based on a certification but more on a voluntary compliance and standard. Using a defined framework where third-party assessment and evaluation is included, greater flexibility can result in more diligence that can be applied to areas that are needed specific to the product or organizational objectives. These organizational objectives can be broken down based on operating modes and risk.
Keep Your Organization Safe from Itself
Whether you choose UL or NIST cybersecurity assessment models to ensure the products you sell are cyber secure, I recommend you do choose one.
According to TechRepublic those who consider themselves tech-savvy are more likely to get hacked. Professionals may have an attitude of "it won't happen to me" due to their knowledge and training, but one moment of complacency is all a dedicated hacker needs to find an exploit. Third-party assessments are the preferred way to keep your organization safe from itself.
About the author: Darnell Washington is the President/CEO of SecureXperts Inc. He is a consultant for over 22 federal agencies and provides subject matter expertise for architecture and infrastructure components establishing Standard Operating Architecture and Common Secure Infrastructure Operating Architecture policy, compliance, governance, and Communications Security for Enterprise applications, including consolidation, server virtualization, operations and maintenance, and deployment of wired and wireless applications.
Washington is the Principal developer and inventor of patented secure enterprise video surveillance product integrating encrypted PKI based security technology with enterprise database security for the Department of Homeland Security and Department of Defense applications.