This article originally appeared in the April 2020 issue of Security Business magazine. When sharing, don’t forget to mention @SecBusinessMag!
Network segmentation is the security integrator’s first and most important line of defense against a data breach. It is a concept and a skill that all integrators will benefit from – particularly smaller independent integration companies and those whose customers are small to medium-sized businesses (SMB).
Network segmentation is the first step to protect everything from a home network, to your own business and your customer’s business.
SMBs are not Cyber-Ready
Many people think small businesses are unlikely to attract the attention of a cybercriminal, which may be a comforting thought, but it is untrue; in fact, small businesses are a favorite target for malicious hackers.
Unfortunately, the notion that a small business is not at risk of cyberattack is all too common. One report found that more than 67 percent of companies with fewer than 1,000 employees having experienced a cyber-attack. The hard truth is cybercriminals do not discriminate against small businesses, and attacks against SMBs are on the rise. 4iQ’s 2019 Identity Breach Report (http://4iq.com/2019-identity-breach-report) found a 424 percent increase in cyberattacks specifically focused on small business.
It gets worse when factoring in what a successful cyberattack will cost a small business. Down time, lost business, regulatory and other fines, damage to reputation: The costs are far reaching and inflict damage that many businesses do not survive.
The status quo for SMBs and cybersecurity is grim, so what can be done?
A lot. And security integrators can play an important role.
The Need for Networking-Savvy Integrators
Physical security integrators have a large responsibility when it comes to securing networks, especially in a routine and relatively simple video surveillance installations. Those integrators who train their staff on network segmentation will be more trusted consultants to their customers. SMBs typically do not have a large IT department; thus, a security integrator who helps them understand and secure their network provides an invaluable service, not only to the customer, but to the safety and security of the Internet at large.
There are many training resources for integrators. CompTIA, for example, offers basic networking and security certifications. Installers who complete those certifications will understand how to architect and secure a segmented network.
The Flat Network Risk
One of the best ways to understand network segmentation is to examine your own home network. Home networks today are actually quite complex, and many are similar in complexity to a network that might be found for an SMB.
Network segmentation is a relatively simple concept that network administrators have routinely applied to business networks; however, network segmentation has become useful in homes because of the explosion of Internet of Things (IoT) devices on the average home network. IoT devices come equipped with various levels of features, support and cybersecurity. According to a study, North Americans will have an average of 13 devices per person by 2021. That’s 52 devices for a family of four. It is easy to forget that each of those 52 IoT devices is a computer with a network interface, storage, memory, processors and an operating system. In addition, these computers are always connected to the Internet, they all have vulnerabilities, and those vulnerabilities are rarely patched unless the device has automated patching.
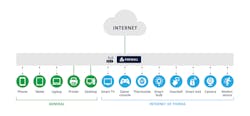
In a “flat network” (see the nearby graphic), devices can all talk and listen directly to every other device on the network; thus, if one device becomes compromised, an attacker can see every other device on the network. If there is an unpatched, vulnerable device on a flat network, it could be the front door that an attacker uses to gain access to the full network.
It is obviously a fundamental risk to keep devices on a flat network. In 2018, a cybercriminal gained access to an Internet-connected thermometer in the lobby of a casino. Once they got access to the thermometer, the attackers were able to pivot the attack and gain access to a high roller database. This would not have happened with the appropriate network segmentation, firewalls and security controls.
Another example is the famous Target breach of 2014, when an HVAC subcontractor installed temperature monitoring software on the Target network. For some reason, it was on the same network as the payment card systems; thus, when attackers gained access to the HVAC system, they were able to pivot and gain access to the payment card systems – resulting in the breach of over 40 million payment card credentials and 70 million customer records.
A Basic Segmented Network
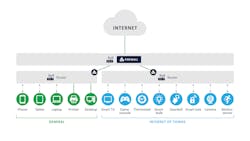
Network segmentation mitigates the risk of flat networks by isolating devices on separate networks. It also conserves bandwidth consumption, secures systems that contain sensitive data, and separates systems from people and other systems that do not need to interact.
For a typical home network, segmentation can be achieved with two or three more routers, or, if you are a bit more advanced in your technical knowledge, using a switch with Virtual Local Area Network (VLAN) capabilities.
To segment using inexpensive routers, see the nearby diagram, where two routers that offer both wired and wireless connectivity are plugged into the main router using standard ethernet cables. The network on the left is for smartphones, laptops, printers, backup drives and any devices that have more sensitive data – this is where you create a guest network for visitors to access the Internet without gaining access to other computers or printers. The network on the right is the IoT network for devices, such as thermostats, smart TVs, cameras and anything else that is “smart” but does not store sensitive data and may not or cannot be updated regularly.
From a cybersecurity perspective, network segmentation isolates problems. If a laptop gets infected with malware, it will not be able to get to the IoT network, because a firewall is in front of that IoT network. The same is true if an IoT device is compromised – the firewall on the general network will protect it from malware infected IoT devices in the same house.
A side benefit of a segmented network is that it uses bandwidth more efficiently. Many people back up their laptops and desktops to network drives. Imagine that this backup is happening automatically in the evening when the laptop is not being used. At the same time, the family is watching Netflix. On a flat network, all of that traffic runs through one router. On the segmented network, the backup happens behind one router while the streaming is all run through the other, which means that the daily backup traffic is not causing the streaming video to buffer.
Additional routers can be added to extend the layers of trust. For example, TVs and game consoles can be separated from light bulbs and thermostats. Devices that are automatically updated can be put on a separate network from those that do not – that way, if a smart fish tank thermometer is hacked, attackers cannot get to your backup drive.Applying it to SMBs
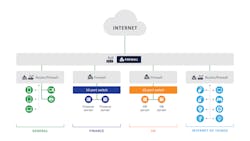
Small businesses typically have the same needs as a modern home network; in fact, in some cases, network segmentation is required by law or standards for the small business. For example, if a business stores, processes or transmits payment and cardholder data, it must comply with the PCI (DSS) standard which among other things, requires proper network segmentation of devices.
A typical network segmentation for an SMB customer.
Learn from Target and the fish tank casino to segment your customers’ networks. The FBI warns that “your fridge and your laptop should not be on the same network. Keep your most private, sensitive data on a separate system from your other IoT devices.”
Integrators should consider requiring staff to get networking certifications such as those offered by CompTIA, as networking credentials can be a differentiator for an integration company in the SMB market. Of course, share networking best practices with SMB customers –in addition to protecting the health of the Internet, you will safeguard their business and your profits.
Chuck Davis, MSIA, CISSP-ISSAP is Senior Director of Global Cybersecurity for video surveillance provider Hikvision. Davis is a former Executive Security Architect for IBM, where he managed the global malware defense and vulnerability management programs. Request more info about Hikvision at www.securityinfowatch.com/10215768.