Editor’s note: This is the 61st article in the “Real Words or Buzzwords?” series about how real words become empty words and stifle technology progress.
Cyber-physical systems (CPS) are computerized systems that interact with the environment around them in physical ways. Securing them can be complicated because of their dual nature (cyber and physical). The purpose of cyber-physical security is to ensure that the entire system works as intended – not just the computing part. It requires both cyber controls and physical controls, as well as a level of due diligence appropriate for the consequences of system failure.
Attack surface is an IT term that we don’t commonly hear spoken in the physical security domain. An attack surface is defined as the total number of all possible entry points for unauthorized access into any system. It includes all vulnerabilities and endpoints that can be exploited to conduct a security attack. Cyber-physical systems have a bigger and more vulnerable attack surface due to their overall complexity and because nowadays they are usually connected to and exchange data with other larger systems.
Complexity Increases Attack Surfaces
Today’s security systems are vastly more complex than in earlier decades. They have more failure points than earlier non-networked systems. For over two decades security investigators have been telling me that 10% to 20% of the time the evidential video they look for isn’t there but should be.
In Chapter 4, “Systems and How They Fail”, of his outstanding book Beyond Fear: Thinking Sensibly About Security in an Uncertain World, Bruce Schneier writes, “Security experts worry more about how systems don't work, about how they react when they fail, how they can be made to fail.” IT folks scan and monitor their networks and devices to get ahead of problems before users experience them because they focus on delivering an excellent user experience, which requires robust IT infrastructure management.
For various reasons, many security industry manufacturers don’t seem to give enough thought to how their products could possibly fail. In other fields of engineering, the opposite is true. Failure Mode and Effects Analysis (FMEA) is part of an engineer’s education and is standard practice in many industries. Read about it at the link above on the website of the American Society for Quality (ASQ).
Attack Surface Exposure
Hackers work to discover both physical and digital access vulnerabilities and failure modes. Many of these are published both on the “surface web” (what search engines index) and on the “deep web” (the unindexed content that’s several hundred times more than the surface web), and especially on the “dark web” (a small fraction of the deep web) that requires a special browser (Tor) to access.
Attack surface access vulnerabilities and failure modes are also the subject of educational sessions at the annual Black Hat and DEF CON hacker conventions, where various hacking contests are held, including lockpicking contests.
Usefulness of the Attack Surface Concept
For those of us who deploy and rely on cyber-physical systems such as those of physical security, the primary usefulness of the attack surface concept lies in two things.
1. Defining the attack surface lets us aggregate a wide variety of vulnerabilities that don’t fully surface during traditional security design, deployment and operations so that we can address them. Defining the attack surface in its entirety enables us to identify, document and properly remediate all the system's digital, physical and functional weaknesses we can find.
2. A key purpose for the attack surface term is to emphasize the attacker’s perspective, which includes accidental and intentional insider threats. We do that (or should) for our facilities in physical security risk assessments. We need to do the same for the protection of our security systems or they will continue to remain vulnerable – which means that our people and assets will be more at risk than they should be due to what we have typically called security system glitches but should really have been labeled security system failures.
There are two kinds of attack surfaces – digital and physical – and our electronic security systems have both. Evaluating the attack surface vulnerabilities involves assessing how security system capabilities can be compromised or misused. Because our physical security systems are based on information technology plus physical sensor and control technology, they are even more vulnerable than business information systems.
Digital attack surfaces for security systems include workstation and server computers, computer operating systems and software applications, networks (wired and wireless), and their points of connection to other systems and the Internet, plus network and software-based points of human interaction such as device and systems configuration.
Physical attack surfaces for security systems encompass all endpoint devices, such as server, desktop, and laptop computers and their USB ports; personal mobile devices; security cameras; intrusion detection sensors and controllers; and access card readers, controllers and their door monitoring and control hardware. A door monitor switch that can be defeated using a simple magnet is part of the attack surface.
How can we effectively approach attack surface protection?
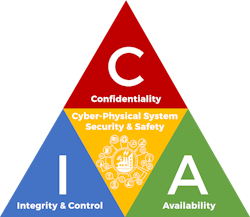
The Security Triad for Cyber-Physical Systems
The Information Security Triad (sometimes just “Security Triad” for short) has provided a rock-solid three-pillar approach to developing a sound cyber security strategy, using the security design objectives of establishing and maintaining Confidentiality, Integrity and Availability (CIA).
I have updated the traditional CIA diagram to add a new perspective – the control element – for cyber-physical systems (See Figure 1). In the event of a compromise of system integrity or functionality, we need to ensure that the system won’t cause harm due to loss or misuse of its physical world control capabilities and that we can be alerted of the failure within and appropriate time frame to manually intervene if needed.
We already have this concept in physical security system design, which we know as the fail safe and fail secure modes.
Cyber-physical systems in many other industries have much more critical failure mode situations to deal with, such as surgical robotic assistance systems and autonomous vehicles, for which millisecond response time can be life critical. But such as in the case of access control and intrusion detection systems, a life-critical situation requiring a response in seconds or minutes could occur.
Figure SEQ Figure \* ARABIC 1. CIA for Cyber-Physical Systems
Image source: © 2022 RBCS, Inc.
Confidentiality
Confidentiality for information systems originally meant restricting data access only to authorized individuals. For cyber-physical systems, this also means controlling access to prevent unauthorized system control and misuse.
Additionally, systems that interact with people may capture data that has privacy restrictions governing it. Some data privacy restrictions are obvious, like for captured biometric access control data. Less obvious are simple records like logs of customer or operator system use that include place and time information and can be linked to a specific individual – because GDPR has defined an individual‘s location data as personally identifiable information and subject to privacy regulations, including information destruction deadlines and anonymizing of data before sharing it with individuals or other systems.
Integrity
Cyber-physical systems and devices are typically part of a “system of systems”, which means that the accuracy of some data can be more important to an external system than to the system or device capturing or generating the data. Often cyber-physical systems serve other systems – both machine systems and people systems – that have a larger purpose and are more impactful in the overall scheme of things.
Consider a city traffic management system that bases intersection traffic light control on counts and speeds of vehicles on the road. Traffic light timing can reduce or increase pollution based on whether it reduces or increases the overall number of brake-then-accelerate cycles. Some cities collect parking lot occupancy data, so that city mobile apps can present estimated valet parking and self-parking availability and direct vehicle occupants to available parking closest to their destination.
Warehouse vehicle-pedestrian accidents have been reduced through the use of forklift and vehicle management systems focused on dangerous intersections, blind crossing points and other hazardous zones. They provide automatic speed reduction or stopping based upon detected pedestrian activity. The integrity of pedestrian activity data is critically important for systems that automatically control vehicle speed and stopping. A failure of intended vehicle control could be catastrophic.
Video surveillance technology can be involved in such scenarios. Increasingly, physical security systems are participating in business operations optimization in addition to their typical security function. In such cases, the larger system’s data integrity depends not just on the accuracy of the data received, but on the continuous operation of that incoming data stream without interruption or system failures. Data integrity or availability issues in a security system could impact the functionality of other systems in many ways, sometimes with larger consequences than the integrity failure had in the security system.
Availability
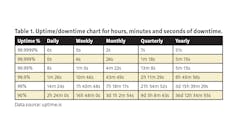
The data center deployments of Amazon Web Services, Microsoft Azure and Google Cloud are exceedingly more complex than physical security system deployments. They offer system availability guarantees of 99.9999% uptime (called “six nines”) for their top-tier cloud services. See the downtime chart below.
Thus, we know high availability is possible and thanks to the advances in cloud computing and information technology in general – high availability is better, simpler to deploy and more affordable than in previous decades.
However, if we don’t demand high availability for our systems, we won’t get it. Security systems should be at least 99.9% reliable (three nines). Why aren’t they?
Undoubtedly, it’s because we don’t treat our cyber-physical security systems (PACS, video, etc.) like IT practitioners treat their critical information systems. We allow only 80% reliability – things working 80% of the time we expect them to, which means 20% failure – to prevail. Security alarms are so unreliable that many police departments now require video verification of an alarm before they will respond.
Today’s AI-enabled technologies can achieve much greater results than were possible in the previous generation of security systems. Now that they are becoming more valuable to security and to business operations, will we finally take action to protect their attack surfaces?
Learn more about attack surface protection at the website of Viakoo, an IT company that entered the IoT industry to help protect IoT attack surfaces and their IoT devices including security video surveillance cameras. Its Service Assurance Manager product is designed to address the problem of missing video and much more.
© 2022 RBCS. All Rights Reserved.