How to Manage Risk and Build Business Continuity that Create Resilience
In the world of business, managing risk takes on many different forms. Whether you are a for-profit business, a non-profit corporation, or a government agency, you have exposure to risk in some form. Managing risk speaks to an organization’s health and its capability to stay engaged in performing its mission, even when faced with adversity.
It means that you are mission ready and capable of producing your products or providing your services at all times. If you are not mission capable, you are out of business. The concept of not mission capable equally applies to the private sector and government entities.
When you consider the impact of risk, you must think about the effects of risk from a broader perspective. For example, a lack of toilet paper is an inconvenience; losing the transportation supply chain is a disaster.Building a Capacity for Risk
Building a capacity for risk and creating contingencies is not a one and done activity; it is a continuous improvement process. According to ISO 31000, an Enterprise should engage the following risk management strategy;
1. Integrate risk management into all business operations and activities.
2. Design an approach that is structured and comprehensive.
3. Customize the risk management framework and resulting process to suit the organization’s goals and context.
4. It is essential to understand the impact of risk on stakeholders, include them in the process.
5. Ensure that the risk management approach is dynamic and robust; also includes preemptive thinking, anticipating, detecting, acknowledging, and responding to changes.
6. The risk management plan must consider any limitations of available information.
7. Realize human and cultural factors are paramount and considered at all stages and aspects of risk management.
8. Understand that the risk management framework is a continuous improvement process that improves through learning and experience.
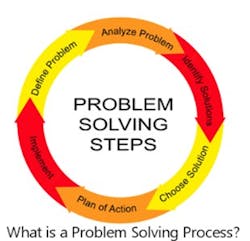
It Starts with a Risk AssessmentAs early as high school, we learn about The “Problem Solving Process” (depicted below). The first two steps of the Problem-Solving process are to Define and Analyze the Problem. To define and analyze the problem requires an all-hazard risk, threat, and vulnerability assessment.
Risk assessment is often considered just to be related to crime and terrorism. In this context, the impact of a natural or accidental disaster can be far more devastating to an Enterprise. A comprehensive risk, threat, and vulnerability assessment will lead to risk analysis, risk evaluation, and ultimately risk treatment.
Resilience and risk management affects every aspect of an Enterprise, including;
1. Security Risk Management
2. Emergency Management
3. Crisis Management
4. Incident Response
5. Information and Network Security
6. Emergency Preparedness
7. Physical Asset Protection
8. Recovery Management
The challenge is to determine how much risk and uncertainty are acceptable and manage the risk and uncertainty while meeting your organization’s strategic and operational objectives.
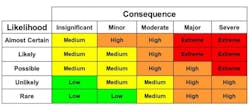
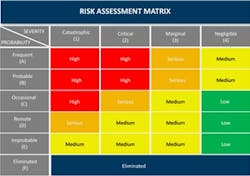
Likelihood, Impact, and ConsequenceThese three concepts are most important as knowing these will help prioritize risk while assessing the impact of uncertainty on achieving Enterprise objectives. Likelihood relates to the probability that something might happen and is measured high to low.
- Impact measures an event’s potential impact on four criteria; financial implications, impacts on equipment, impacts on people (injury or death), and impacts to internal and external stakeholders.
- Financial impacts are simpler to discern as they are pretty straightforward; a budget supports a potential event or exceeds the financial capability of the Enterprise.
- Equipment impacts are directly tied to the critical equipment that is needed to produce products and services.
- Impacts to people focus on events that can cause injury, illness, or death.
- Impacts on stakeholders are a measure of public confidence in producing reliable products and continued services in the face of adversity.
To know these items requires intimate knowledge and directly correlates the impact of consequence on the Enterprise. Understanding threats and their consequence help to identify the value and need for a contingency plan.
Vulnerability: The term vulnerability relates to present preparedness levels in equipment, people, processes, plans, policies, procedures, and training that support the Enterprise in a risk-based event. It is vital to remember that the previous items are only valid if trained, practiced, and exercised. We will discuss training a bit later in this article.
Calculating Risk: Knowing the threat, consequence, and vulnerability is required to calculate risk. There are many formulas for calculating and depicting risk. The simplest way is to use a heat map to demonstrate where your highest risks reside.Treating and Mitigating Risk: Having identified the most impactful and critical risks to the Enterprise, it is now time to minimize or eliminate the risk. We accomplish this by discerning mitigations or risk treatments.
Risk Treatment: Risk treatments are effective, appropriate, and realistic steps to protect against the most severe threats and risks. Risk treatments are many but are generally categorized into plans, processes, people, and equipment.
A risk treatment related to plans might include planning for a potential event, such as actions to be taken by people during a human-made (crime and terrorism) event, natural disaster, or accidental hazard. Planning includes all activities required to prevent, protect, prepare, mitigate, respond, and recover from a risk-based event.
Processes might include the workflows which are needed to address the details of a risk-based event. An example is the processes, methods, or technologies used to notify employees of contingencies or when and who to call when emergency services are required.
When considering the people aspect, we refer to the training and expectations of plans, policies, and procedures. Exercises follow the training to ensure training objectives are translated into appropriate action for a given event. There are seven types of exercises: seminars, workshops, tabletops, drills, functional exercises, and full-scale exercises. Exercises are progressively more complex, starting with individual skills and culminating with extensive collective activities that have many moving parts.
Equipment speaks to supplies, technologies, vehicles, specialized tools, and other logistical items needed to accomplish our plans.
Gap analysis: The current state of preparedness to respond to risk and what the to-be state will be post-training and exercise, including all the activities required to get us from where we are to where we are going, are referred to as the Gap.
Risk Treatment Plan and Gap Analysis
Closing the gap requires applying a risk treatment, necessitating a plan for implementing the risk treatment. The Risk Treatment Plan spells out how the risk treatment is implemented, helping all stakeholders understand and measure implementation progress.
Your risk treatment plan should include:
• The reason for selecting the risk treatment option
• The benefit(s) you expect from implementing the risk treatment option
• The people accountable and responsible for approving the plan
• The people accountable and responsible for implementing the plan
• The actions involved in implementing the risk treatment
• All resources required for implementation, including contingencies
• The performance measures to be monitored and evaluated
• Constraints
• The plans for monitoring and reporting
• The schedule/timetable/deadlines
Risk Registers: Tracking risk treatments necessitates the use of a project management tool called a Risk Register. There are many different templates for a Risk Register. Ultimately, the intent is to keep the Enterprise focused on the goal, preparing for a risk-based event. A sample form is below;Business Continuity Planning
Business continuity is the Enterprise’s ability to carry out their everyday activities and functions in the face of adversity. Some potential events could be a pandemic, a business crisis, natural disasters, or even workplace violence. Previously in this document, we have identified the need for a risk assessment and impact analysis. In this section, I will provide definitions for both business continuity and a Business Continuity Plan.
According to ASIS International, in its Business Continuity Guideline (ASIS GDL BC 01-2005) we find the following definitions;
“Business Continuity is a comprehensive managed effort to prioritize key business processes, identify significant threats to normal operation, and plan mitigation strategies to ensure an effective and efficient organizational response to the challenges that surface during and after a crisis.”
“A Business Continuity Plan is an ongoing process supported by senior management and funded to ensure that the necessary steps are taken to identify the impact of potential losses, maintain viable recovery strategies and plans, and ensure the continuity of operations through personnel training, plan testing, and maintenance.”
A Business Continuity Plan contains the following components;
- Document Control
- Scope
- Objectives
- Risk Assessment of Impact Analysis
- Invocation Process
- Incident Management Team
- Key Roles and Responsibilities
- Communications Planning
- Disaster Recovery of Information Technology Systems and Information Backup
- Human Resource Considerations for Staff Welfare and Regulations
- Alternative Locations
- Inbound and outbound supply chain
- Activation Procedures
- Checklists
Federal Emergency Management Administration (FEMA) Business Continuity Plan Template https://www.fema.gov/sites/default/files/2020-10/non-federal-continuity-plan-template_083118.pdf
Creating Resilient Enterprises
Resilience is an Enterprise’s ability to adapt to a change quickly, efficiently, and effectively, such as disruptive events (natural, intentional, or unintentional), by implementing adaptive, proactive, and reactive strategies. All organizations face a certain amount of uncertainty and risk. To ensure continuity of operations and maintain resilience, competitiveness, and performance, organizations must have a system to manage their risks. The challenge is to determine how much risk and uncertainty is acceptable and how to cost-effectively manage the risk and uncertainty while meeting the organization’s strategic and operational objectives.
At the onset, this can be a daunting process, but there is a reward for engagement. Rewards are realized in fewer surprise events, exploiting your preparedness when your competitor is unprepared, improved performance and effectiveness due to more functional teams, an excellent reputation with your stakeholders, and ensuring Enterprise longevity.
Continuous Improvement
Please understand that this is not a one-and-done process. Building a plan and creating a resilient Enterprise takes work. Many factors generate the need for a review, including a new risk assessment that identifies previously unknown issues, industry trends and compliance requirements, lessons learned from exercises, and lessons learned after an actual event. Any of these indicate the need for a plan review.
Moving Forward
The process of creating a resilient enterprise is not easy, but it is rewarding. It takes involvement from many different aspects of the Enterprise. In my opinion, the most important is a commitment from management to protect critical assets, provide resources, and engage in continuous improvement.
To start, create a vision, detail what success looks like, develop metrics to quantify success, keep your eye on the long term, and celebrate your accomplishments. Understand you can’t eat a whole pie at once, but you can enjoy each bite.
About the author: Jeffrey A. Slotnick, CPP, PSP is President of Setracon ESRMS. He is an internationally known Enterprise Security Risk Consultant with more than 28 years of experience, peer-recognized as a “Thought Leader” and a “Critical Architect in homeland security”. As an ISO credentialed Lead Auditor Jeff is responsible for some of the latest advancements in All-Hazards Disaster Resilience, Organizational Resilience Management, ISO/ANSI Standards Development, Resiliency Information Management Processes, and Enterprise Security Risk Management.
Jeff is focused on the professional development and training of security, law enforcement, and military personnel, the provision of exceptional security services, protective services, and all facets of Enterprise Security Risk Management. Jeff is a Senior Regional Vice President for ASIS International, Faculty Advisor for the University of Phoenix Bachelor of Science in Cyber Security and Security Management Degree Program, a member of the Risk Management Society and a 20 year Reserve Law Enforcement Officer for the City of Centralia, Washington. [email protected]