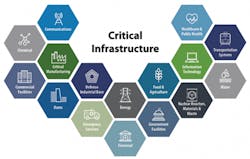
What is Critical Infrastructure?
“Attack [your enemy] where he is unprepared, appear where you are not expected.”- Sun Tzu
Asking a cross-sectional group of officials to define “critical infrastructure” would be like asking the group to close their eyes, think of a dog, and describe what they saw. We would end up with answers that range from a Chihuahua to a Great Dane. Just like solving complex problems, we have to recognize the problem, define it, and then proceed with solutions to solve it. It is the same with critical infrastructure protection – we need to recognize and define what CI is, the who, where, when, why, and how.
The term Critical Infrastructure seems to have morphed and been applied in several contexts. The IT world thinks of the networks, and others, in the realm of power generation, we hear it in the sense of transportation systems…highways, bridges, and tunnels – the list goes on. The positive aspect of this phenomenon is the term is widely known and applied in promoting resiliency programs or prioritizing “business criticality,” but challenges occur when outlining roles and responsibilities, strategies, organizational design, policies, technology, R&D, obtaining and applying resources, training, and much more.
The best starting point is to apply how the Department of Homeland Security (DHS) defines Critical Infrastructure –
This is a good start-point covering the physical and virtual worlds which don’t always align, but the definition seems government-focused.
The strategic approach that governments, businesses, and other private sector organizations extend to, stems from the National Infrastructure Protection Plan (NIPP) which was promulgated under Presidential Policy Directive – Critical Infrastructure Security and Resilience (PPD-21).
PPD-21 in the broad sense designates 16 Sectors, further divided into Sub-Sectors that are the “essential services that underpin American society…that are vital to public confidence and the Nation’s safety, prosperity, and wellbeing”. Similarly, just as the United States relies on its critical infrastructure for national and economic security, the same applies to any country’s interests.
The sector and sub-sector categorization provide institutional leadership along with the responsible components - security, crisis management, business continuity, first responder, emergency management, and security industry practitioners with the foresight and direction to safeguard the essentiality of their organizations and clients to best plan, prepare, support and respond.When the Stars Are Aligned
“The truth is that you always know the right thing to do. The tough part is doing it.” – General Norman Schwarzkopf, U.S. Army
Prior to the Information Age, security was predominantly one-dimensional - the protection of assets. Assets can be described along many lines of thought, but it was generally the basics - locking items up and controlling access. This can be said about anything when it comes to security. But in the age of information technology, advanced threat capabilities increased the need for sophisticated and technical security tools and techniques.
The growth in threat vectors and protective needs have created the two security universes of physical security and cyber/information security. The divide lies in many organizational constructs, resource priorities, and talent ratings. What it has also created is two separate security groups with independent reporting chains in many organizations. This is unlike many other specialty practices which are usually uniform under a central management structure, i.e., Legal, Human Resources, Finance, Communications, Corporate/Shared Services, etc.
We keep hearing terms like “convergence” as well as GRC – Governance, Risk, & Compliance, or TRM – Third-Party Risk Management, but questions beg about how it is authentically and suitably applied. A good example is taking what may be the simple term “Access Control.” Whether it is physical access or virtual access, the same standards should apply. Unfortunately, the practices and more so the compliance and audit standards are sometimes worlds apart.
Organizations would never consider approving unfettered access to an organization's network. On the flip side, coming up with strict standards for controlled visitor access, outside service personnel, or after-hours access to outsourced cleaning services are a few examples, which can turn into a cataclysmic event for security practitioners, or more so, physical security practitioners accused of delaying, denying, or creating unnecessary controls where end-user objectives are to quickly grant access for individual business requirements. What a novel idea that access control, identity management, visitor management, vendor/contractor access, encrypted credentialling, intrusion detection/prevention, lock and key controls, security monitoring, and much more are aligned across the board with similar standards and control measures.
Security is security – convergence is a practice where security organizations, protocols, funding, operations, investigations, and training should be considered unified under a single governance and management structure. Employment law groups do not fall under HR nor do contract law works under procurement; cybersecurity should be aligned in the same manner, as opposed to autonomous controls from a holistic and converged security construct. As with any asset, the process owners are responsible for the protection of the assets they manage in line with an independent authority.Revisiting the Design Basis Threat (DBT)
“If you fail to plan, you are planning to fail” – Benjamin Franklin
Security and resiliency priorities tend to sway towards the immediate or locality, with varying views of the past and the future. Even compliance and risk-based requirements can be easily disregarded due to a lack of historical context, meaningful audit, and hollow consequences.
The DBT is a description of the type, composition, and capabilities of an adversary, against which a security system is designed to protect. It is a more direct approach to a security framework. DBT relieves an additional exposure of putting faith and reputation into risk probabilities, but more directly into defining protective measures. A good example is CBRNE protection – Chemical, Biological, Radiological, Nuclear, and Explosive. Risk models, will most likely rate CBRNE as low-probability/high-impact, but leaves the question - should detection, assessment, and protection measures be ignored or in the low-to-zero priority in the resource rankings, particularly in densely populated, high-profile locations (i.e., airports, mass transit, stadiums, iconic landmarks, etc.)? It’s like managing the risk of risk management.
Throughout history and more recently as we changed centuries, we have experienced events and tragedies that past and present generations would reject or argue its likelihood. After the Soviet Union collapsed, Western powers reversed a Cold War readiness posture; 9/11 was considered by many as a “black swan” event and would have been rejected on 9/10; and the attitude of the Global Pandemic was initially viewed only as a Chinese problem. These are some significant events, but it translate into everyday decision-making when it comes to protective strategies and our critical infrastructure. A reoccurring deniability that bad things only happen to others is a reverse over previous positions we will have peace and stability in Europe, terrorism died with Bin Laden, or sounding the alarm of a pandemic was only an incitement of panic until it spread like a tsunami all over the world.
The reality is that bad things do happen. Environmental threats and accidents can devastate any place, at any time. Bad people are out there who prey on our industries and communities. Threat actors come in many forms from street criminals to nation-states; unskilled to skilled adversary; and home-grown violent extremists to transnational terrorist groups. Our society no longer views school shootings as an isolated occurrence that only happens in other communities – all schools now protect their students and employees for the worse. Weapons of Mass Destruction (CBRNE) attacks are still rated as highly credible. Similarly, there is a public expectation that governments anticipate consequences and are prepared. Customers, employees, shareholders, and board expectations are that companies and institutions are equally demanding and unforgiving with failures to anticipate, resource, and prepare for the unexpected.
Risk management calculations are still a useful tool to apply a formula for measuring risk and threat probabilities from high to low, but it will never eliminate the threat and threat capabilities. The DBT methodology provides a more realistic approach of what is lurking to guide decisions when designing protective strategies.
Partners for Readiness
"Security is always seen as too much until the day it is not enough." – Judge William H. Webster
Another challenge faced with critical infrastructure protection is resource constraints to maintain a readiness and protective posture. Within any organization, public or private sector, requirements normally exceed resource allocations…people, equipment, technology, and training.
Many organizations, mostly within government agencies, attempt to maintain a protective, readiness, and response posture by having adequate sets of equipment in use and on-hand for elevated events. Private organizations are more fiscally constrained. Outside of government, stockpiling emergency management and disaster response equipment is rarely accepted as favorable. Paying for equipment that may never be needed or protecting against a threat situation that may never occur have been acceptable risks.
The next best strategy to overcome resource constraints is to have “partners for readiness.” This is interpreted by having the relationships and pre-established rapid acquisition contract vehicles to reach over to selective logistics partners which can rapidly supply the equipment, technology, training, and transportation when the crisis occurs. This can be best phrased as partnering with services with a proven record for “Just In Time Inventory and Supply Chain.” The proven benefits provide a centralized procurement and pre-negotiated sourcing strategy for day-to-day requirements, with the ability to immediately ramp up when a crisis hits. This is planning. This is readiness.
Protecting the Future
“We have met the enemy and he is us” – Pogo
Threats to the Homeland are not subsiding from abroad and within. Protecting the US Critical Infrastructure, our people, and our way of life will always be a challenge when debating requirements, priorities, and resources. Regardless, expectations remain high among a wide constituency of stakeholders. Those of us who are in the security industry will continue to promote approaches, products, technology, and services. The key to the future will be innovation - shifting from paradigms that may have limitations and breaking into something new and different. We have transitioned from the Industrial Age to the Information Age, and now it is time to embrace the Age of Innovation.